What is PiHole (Version 5)?
fyi: I updated this post 3 months after I created it as I killed my 32GB Raspberry Pi Micro SD card when I pulled the power (before a storm) without shutting down the Raspberry PIU first. Always shutdown the pi before removing the power. I have a 16GB Micro SD card that I will use instead.
I am following my guide to re setup up my PiHole.
Snip from WikiPedia: “Pi-hole is a Linux network-level advertisement and Internet tracker blocking application which acts as a DNS sinkhole (and optionally a DHCP server), intended for use on a private network. It is designed for use on embedded devices with network capability, such as the Raspberry Pi, but it can be used on other machines running Linux and cloud implementations. Pi-hole has the ability to block traditional website advertisements as well as advertisements in unconventional places, such as smart TVs and mobile operating system advertisements.”
What is a Raspberry PI?
A Raspberry PI is an inexpensive (5V Volt, 2 Amp) ARM based computer that can run off the power from a USB cable.
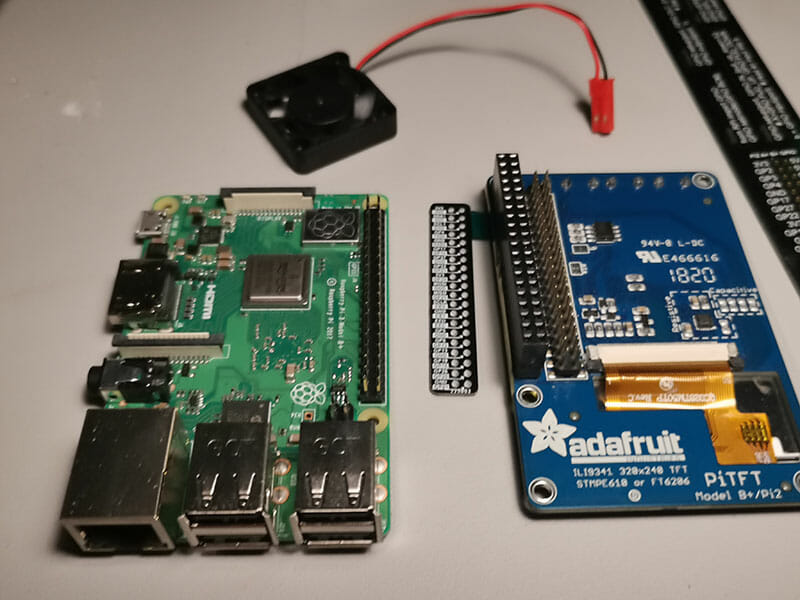
Here is a photo of my Raspberry Pi 3B+ with an Adafruit LCD Screen
My Raspberry Pi has the following specifications
- 4 x 1.4GHz 64-bit (quad-core processor)
- 1GB LPDDR2 SDRAM
- Dual-band wireless LAN
- Bluetooth 4.2/BLE,
- Faster Ethernet
- Extended 40-pin GPIO header
- Full-size HDMI 4 USB 2.0 ports
- 5V/2.5A DC power input
My screen has the following specifications (purchased from Pakronics)
- 3.5″ display with 480×320 16-bit colour pixels
- Resistive touch overlay
I plugged in a full sized USB Keyboard, Mouse and HDMI cable.

SD Card Choice
Read my guide to download and write an Raspberry Pi Operating System to an SD card.
I would not put a cheap/slow MicroSD card in the Raspberry PI, aim for at least a UHS (1) or UHS (3) speed SD card for the best bang for buck.
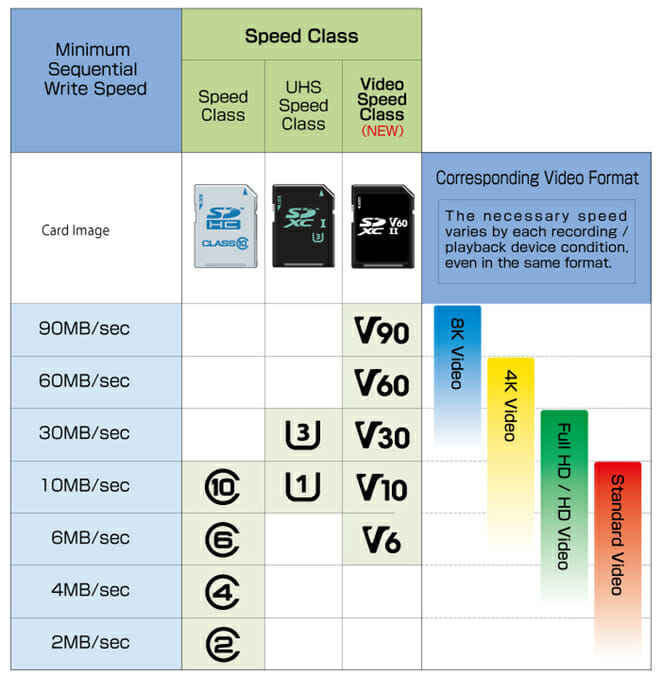
fyi: I bought a new 32GB Samsung UHS 1 Ultra Micro SD card and it died after 12 hours of use. I replaced it with another 32GB No name brand CLASS 10 SD Card I had laying around.
(after I killed my 32GB Micro SD card I have chosen a 16GB Micro SD card as it is all I have spare)

Raspberry Setup
I download and saved the Raspian (Full) Operating System to a SD Card and inserted it into my Raspberry PI 3B+ (view the guide here on preparing an Operating System on a SD card).
I used the American 110-240V AC to 5.25V 2500ma DC power supply (with a US to AUS adaptor) that came with the Adafruit Screen. It had a Micro USB connection on one end.

It did not work though (I just had a flashing red light on the Raspberry Pi).
I had an Australian 240V AC to 5V 2500ma DC power supply to Micro USB. from a previous project and it worked (the Raspberry Pi Started up).

I also have a number of Moki brand 240V to USB (1A and 2.4A) adapters.
I will use the 2.4mA plug. I know my Adafruit screen uses 100mA so this will do.

I plugged the HDMI cable into my Monitor and set up the HDMI as a Picture in Picture output so I can see my Main 4K screen (Display Port) and the Raspberry Pi HDMI input at the same time.
My First Raspberry Pi Boot
Mmmm my 4K screen with a 1080P HDMI picture in picture image (from the Raspberry Pi).
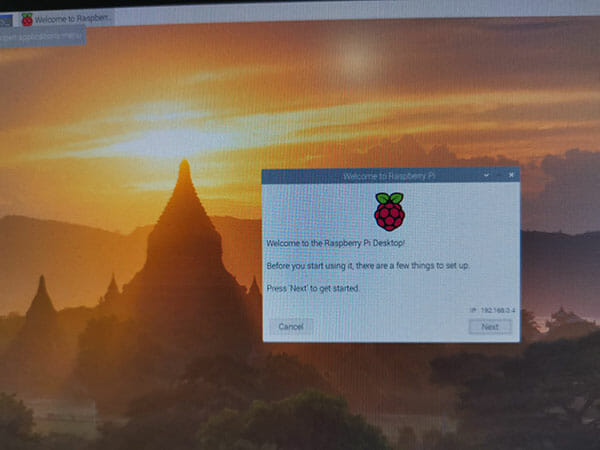
The Raspberry Pi booted fast and a welcome screen appeared
Apologies in advance, photos below are bad (I don’t have a HDMI capture card).
I clicked Next to setup the Raspberry PI
I set my timezone and language
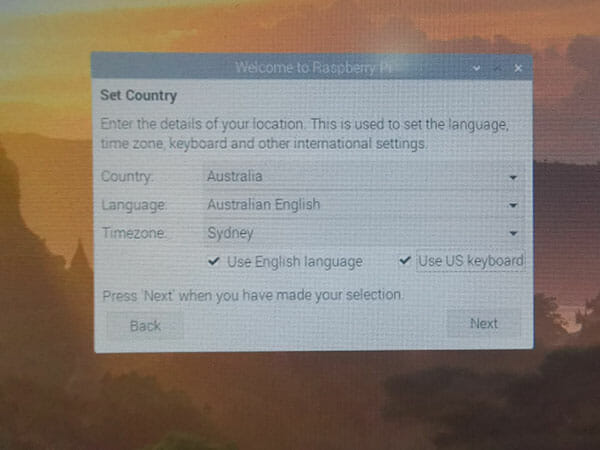
I set a password
I skipped connecting to WiFi (I want pure Ethernet)
I was prompted to update the software (I clicked Next)
Setup is complete
I rebooted the Raspberry Pi
Second Boot
I changed further configuration by clicking the Raspberry Pi start button then Preferences then Raspberry PI Configuration
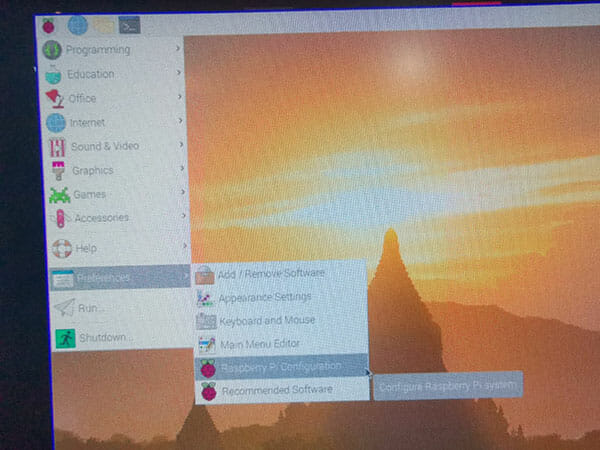
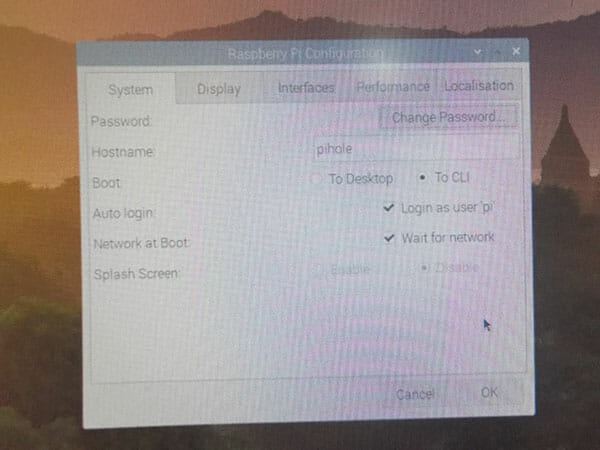
I changed the hostname to “raspberrypihole”, set Boot to CLI , Login as “pi“, and set Wait for network.
Update: After my Samsung SD card died I re setup my PI with a no name brand SD card and entered the name “raspberrypihole“
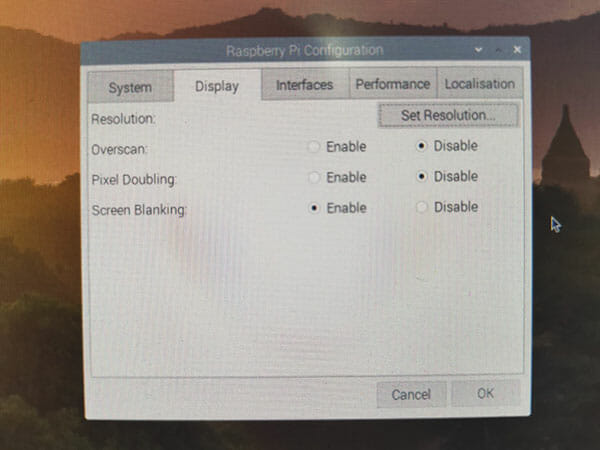
Under display I reviewed the display options
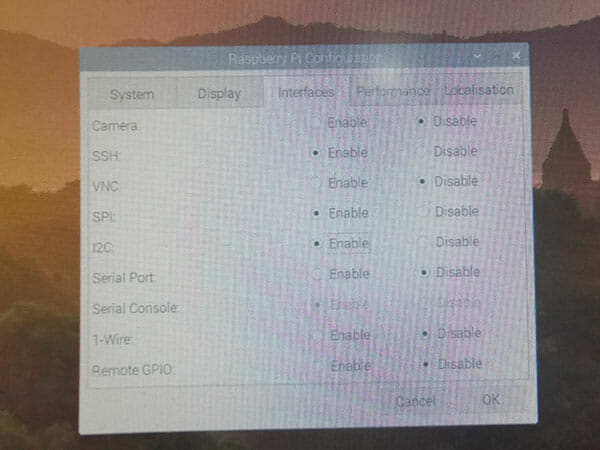
I enabled SSH, SPI and I2C.
I increased the GPU memory to 132GB
Time for a Reboot
SSH Access
I do not want to leave a keyboard, mouse and screen connected once I finish setting it up so I setup a SSH connection to the Raspberry Pi.
TIP: Putty is a free program for SSH connections.
I SSH’ed (more information on SSH below) to the Raspberry Pi and ran these commands to update it’s software and firmware.
sudo apt-get update && sudo apt-get upgradeOutput
pi@raspberrypihole:~ $ sudo apt-get update && sudo apt-get upgrade
Hit:1 http://archive.raspberrypi.org/debian buster InRelease
Hit:2 http://raspbian.raspberrypi.org/raspbian buster InRelease
Reading package lists... Done
Reading package lists... Done
Building dependency tree
Reading state information... Done
Calculating upgrade... Done
0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
The program “htop” is good for viewing system resources.
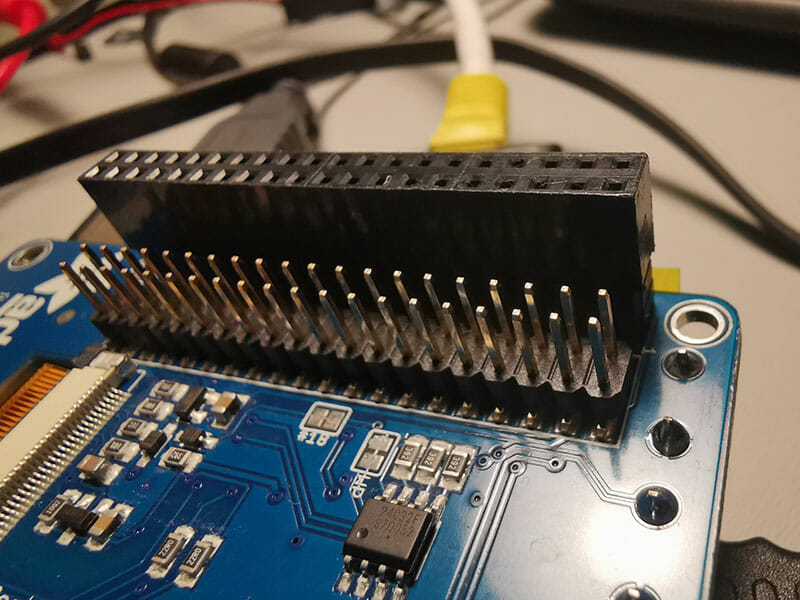
Now it’s time to look at the Adafruit screen and case.
I put the Raspberry PI in the Adafruit Case
I purchased this kit for the Raspberry Pi, the LCD screen just connects to the Raspberry Pi GPIO pins. It has a Adafruit LCD screen and a case for my Raspberry Pi 3B+

The screen just connects onto the GPIO pins

The LCD screen allows you to use pins below the screen.
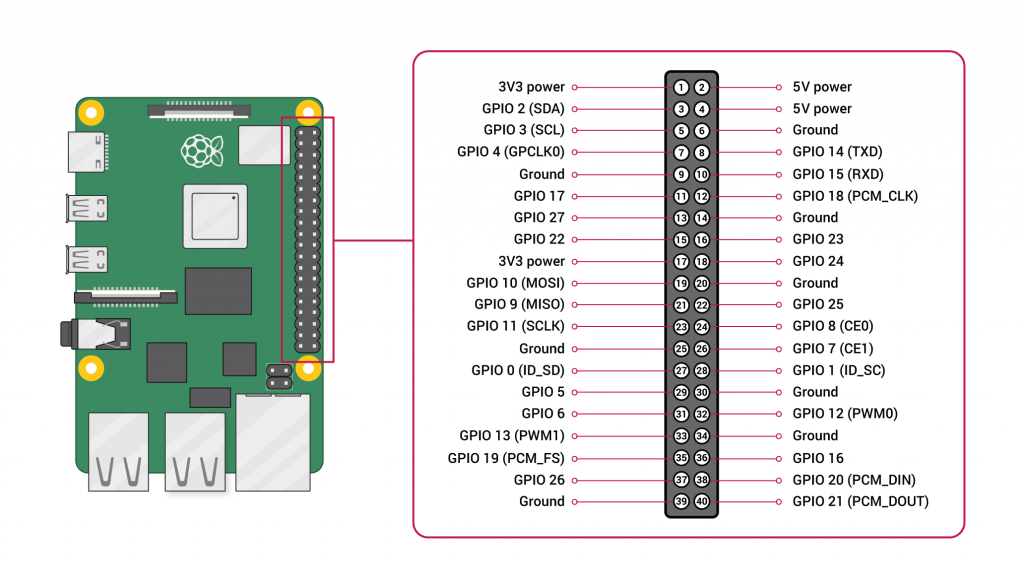
GPIO pins documentation from https://www.raspberrypi.org/documentation/usage/gpio/
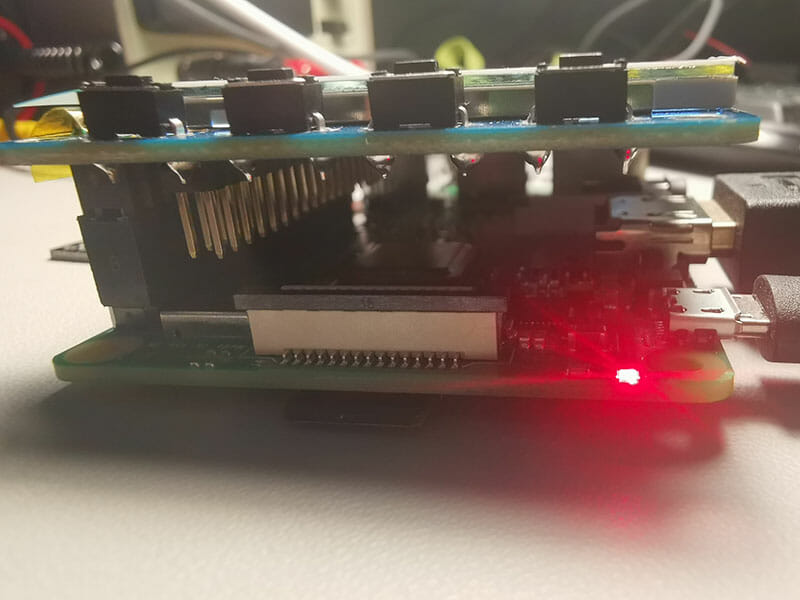
A nice stack 🙂
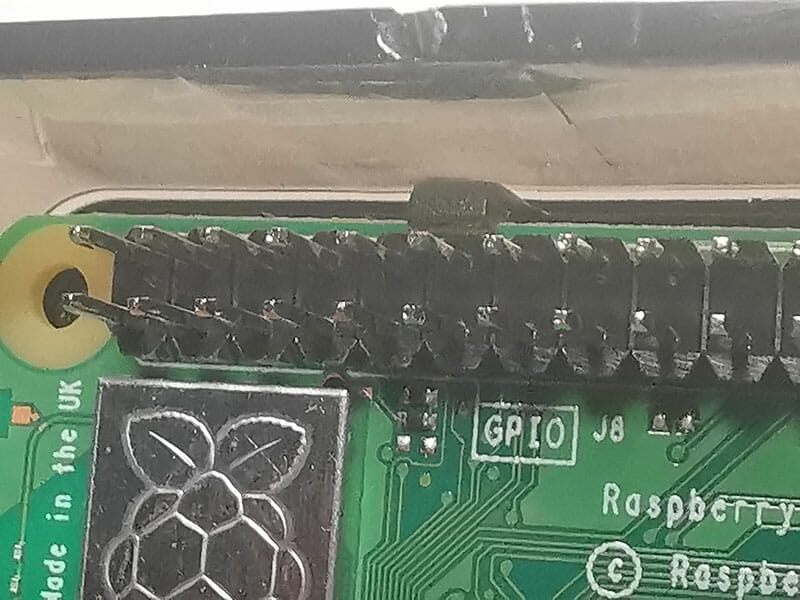
The case clips are hard to clip over the Raspberry Pi (Don’t force it or you might break for Pi)

The case clip near the GPIO pins is on
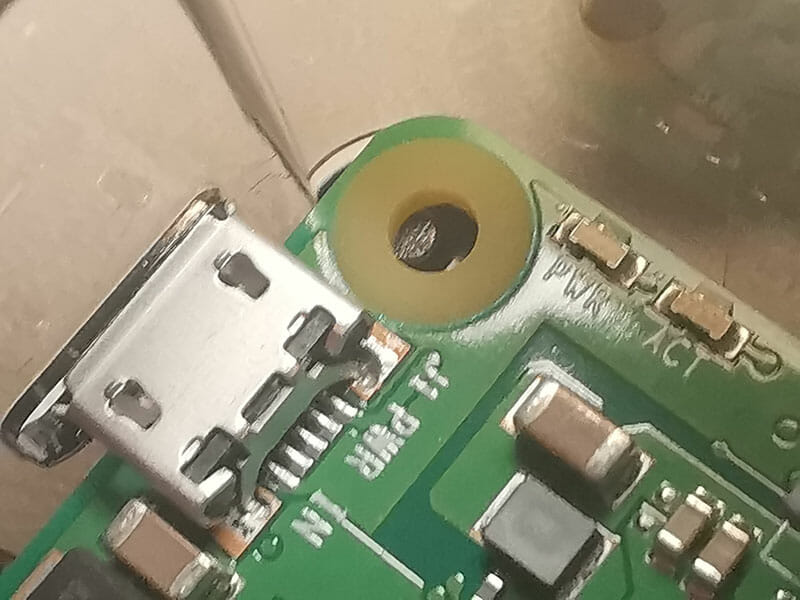
The clip near the power plug was off because the Raspberry Pi was not positioned correctly
After 30 minutes I carefully put the Raspberry Pi and LCD screen into the Case.

Side of the case with USB and Ethernet and USB porws exposed.

HDMI, Power and Audio plugs are visible and lined up 🙂

The screen is visible through the case

The screen dips down on one side, I might have to prop it up (hot glue gun) a bit inside later

SSH Connections to the Raspberry PI
I created an SSH connection to my Raspberry PI with MobaXterm (review here) and connected to it.
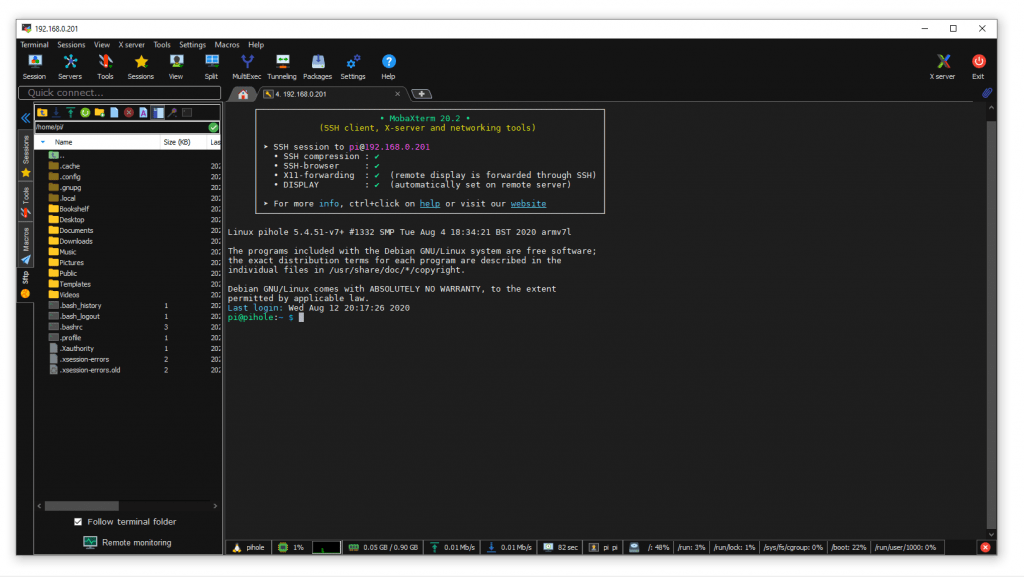
I ran the “ifconfig” command to get a list of all network interfaces.
I ran “ifconfig” to list all network interfaces.
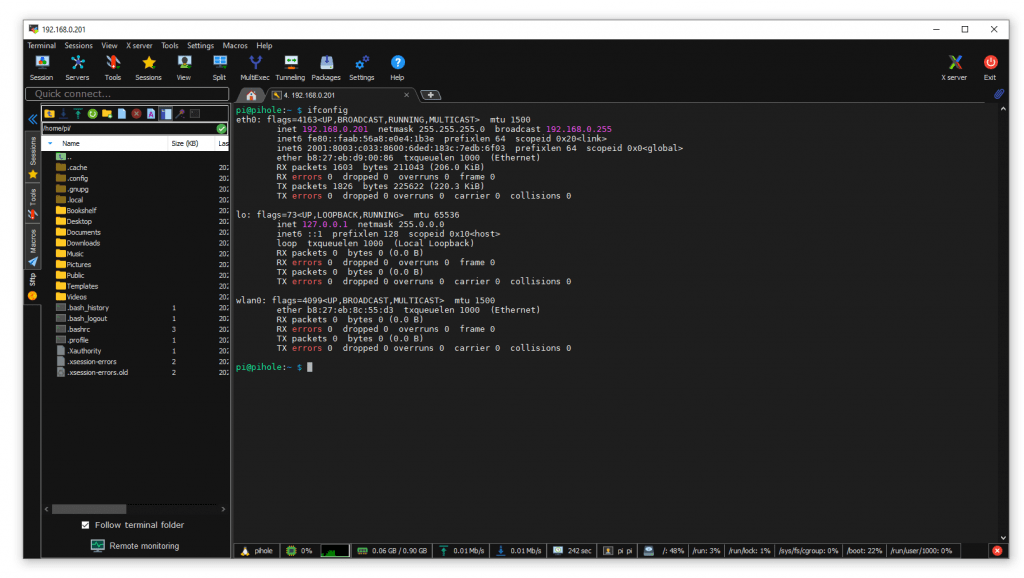
I ran these commands to update my Raspberry PI Software
- sudo apt-get update
- sudo apt-get upgrade
- sudo apt full-upgrade
- sudo apt -y dist-upgrade
I updated the Pi Firmware too (this is dangerous, only update if you have issues).
- sudo rpi-update
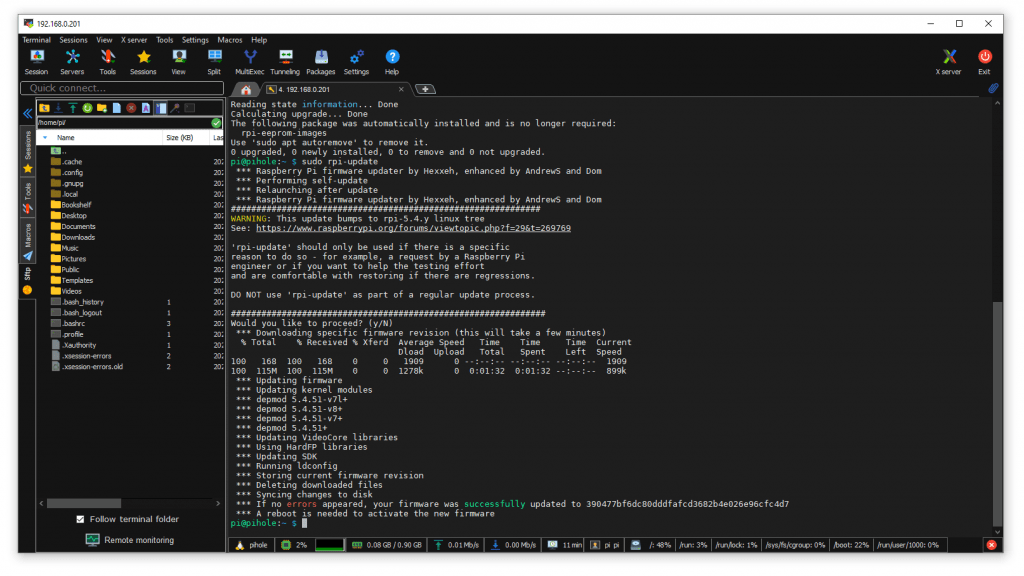
I rebooted and connected to the Raspberry Pi and ran this command to get the Ethernet and wireless mac address.
The first interface is my Ethernet adopter the second if the WiFi adaptor.
ifconfig |grep ether
ether b8:27:eb:d9:00:86 txqueuelen 1000
ether b8:27:eb:8c:55:d3 txqueuelen 1000The first Mac address is my Ethernet address on The Raspberry PI and the second is WiFi.
I logged into my router (Telstra DJA0230) and clicked Advanced then Local Network. I could see my DHCP range was from 192.168.0.2 to 192.168.0.254, I shortened this to 192.168.0.2 to 192.168.0.200 (so I can set a static IP Address for the Raspberry PI) then I set a Static IP address for the Raspberry pi to 192.168.0.201.
I rebooted the Raspberry PI and checked the IP address
I logged into my Router (at https://192.168.0.1)
When my Samsung SD card died I had to re-setup a new SD card but the IP address came across as the mac address stayed the same (as it was the same hardware), I did, however, change the name of the Static IP hostname in my home router to match the new name “raspberrypihole” (not “pihole”)
I set a static IP for this Ethernet address and defined 192.168.0.201 as the IP address.
Setting Up PiHole on the RaspBerry PI
I SSH’ed to my Raspberry Pi (with the new IP address) and ran this command
Now its time to install Pi Hole onto My Raspberry Pi
wget -O basic-install.sh https://install.pi-hole.net
sudo bash basic-install.sh
I was presented with “This installer will transform your device into a network-wide ad blocker! “
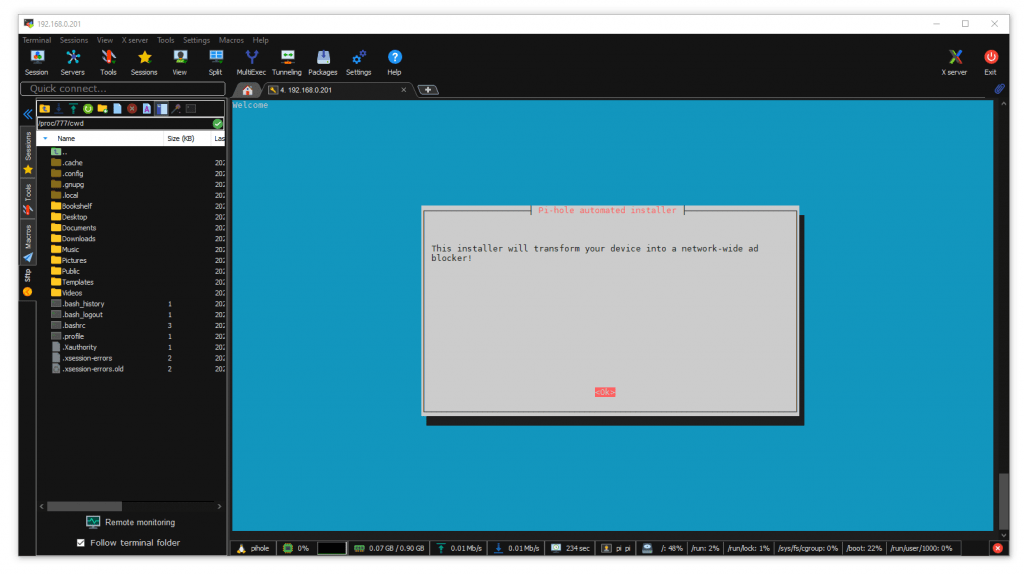
I was presented with “This installer will transform your device into a network-wide ad blocker! “
PiHole is free, but powered by your donations (consider donating)
I donated. Thanks PiHole Team.
This will pay for itself in no time.
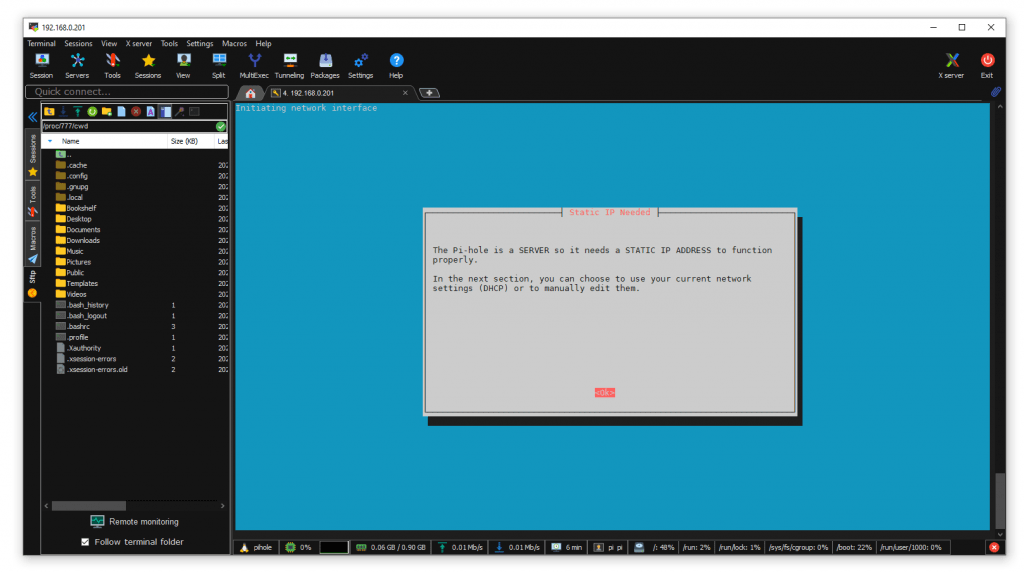
Static IP address is required.
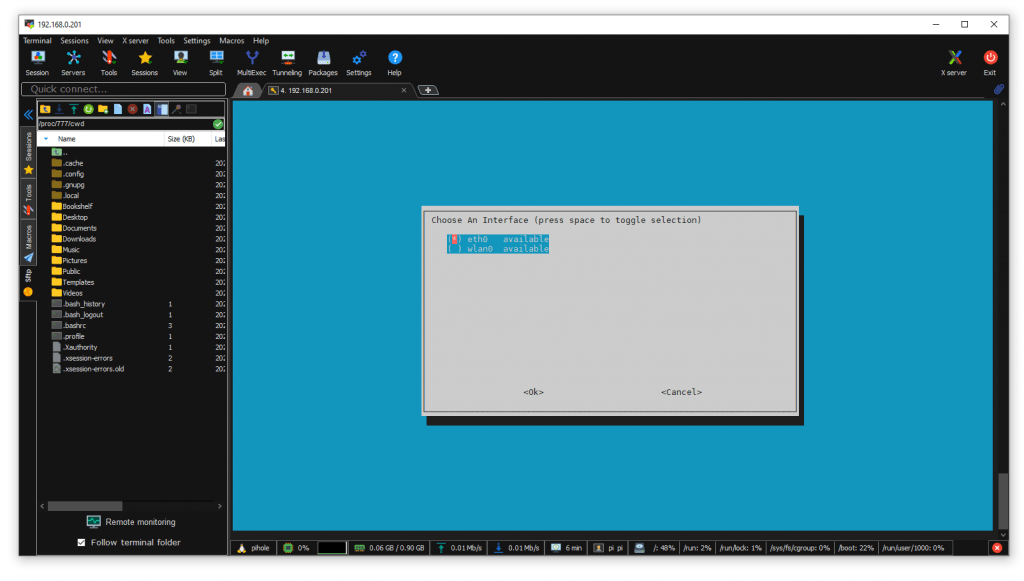
I chose to just have PiHole work on Ethernet (and not Wifi)
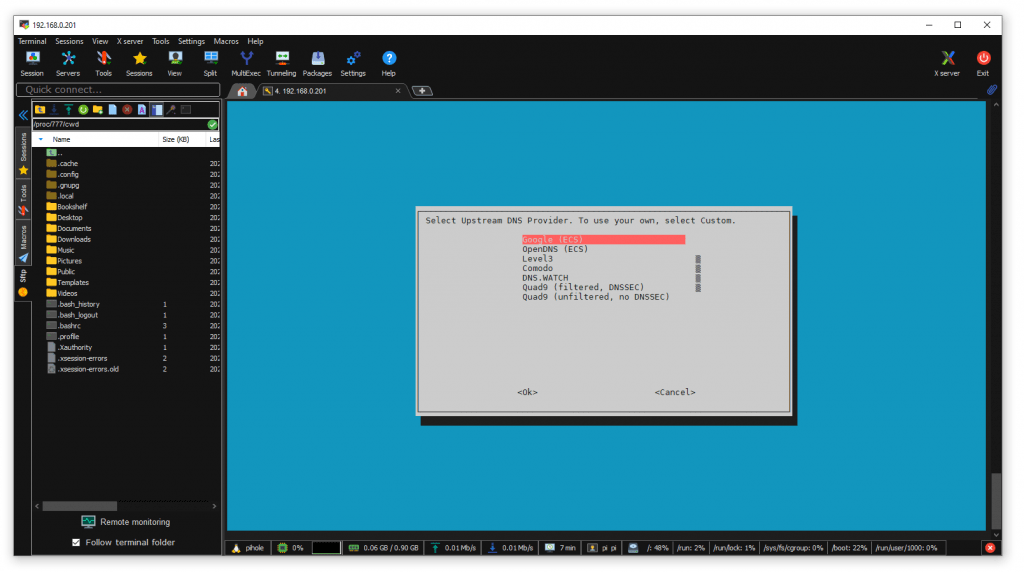
I was prompted to set my upstream DNS provider.
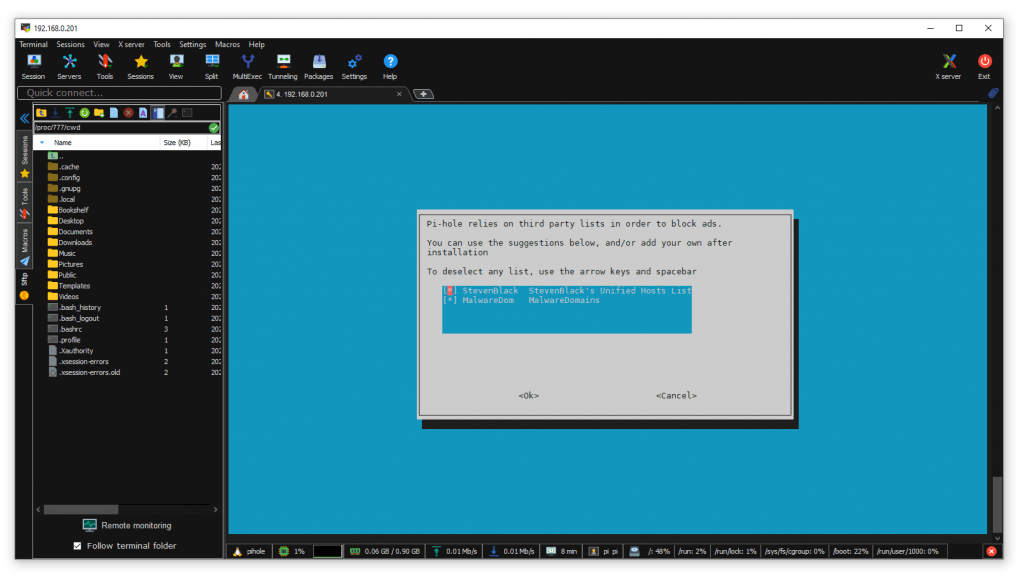
I selected all default blacklist lists.
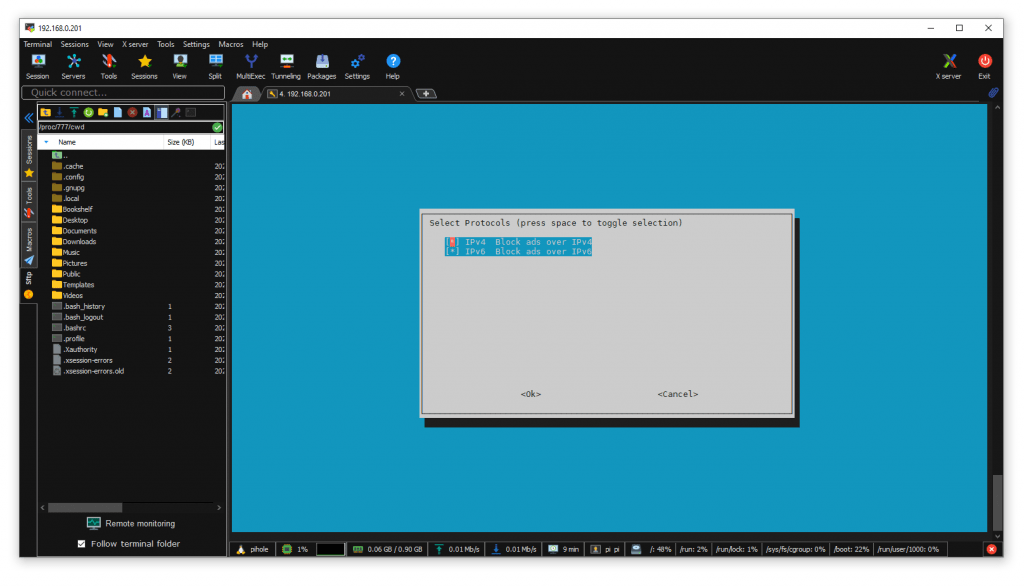
I allowed PiHole to use IPv4 and IPv6.
My IP and Gateway was displayed on the screen.
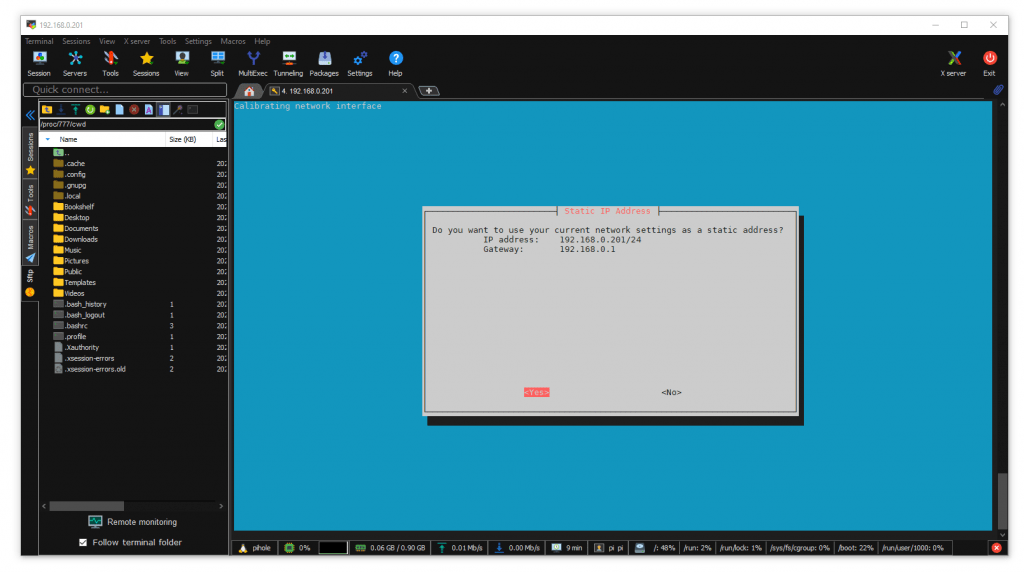
Final warning about setting a static IP address.
The PiHole IPv6 address is show
Install a admin interface (Yes)
Install lighthttpd (Yes)
I chose to log all DNS queries.
I oped to allow the viewing of all logged data. This is less secure but I can reduce this later.
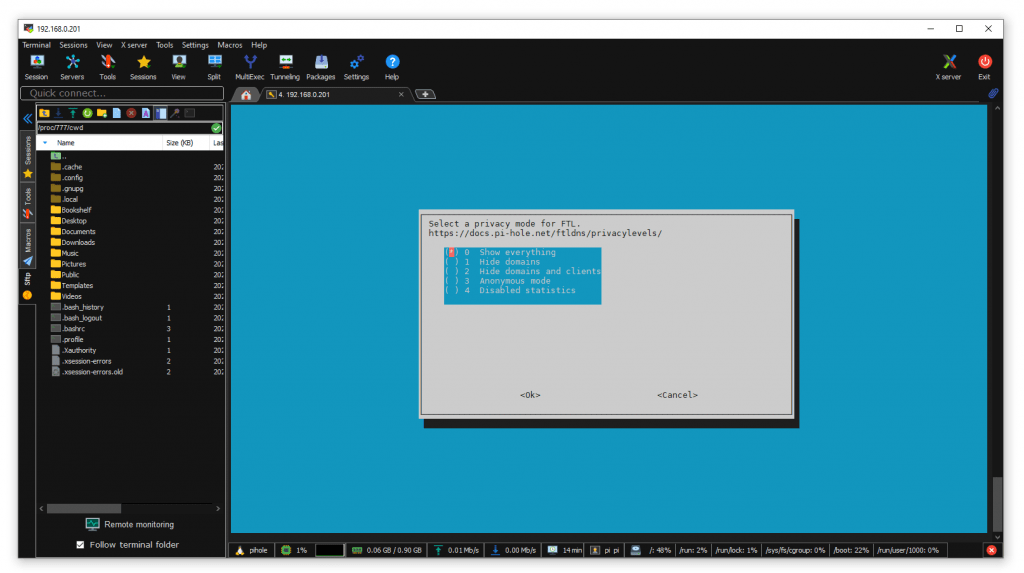
PiHole is now setting up
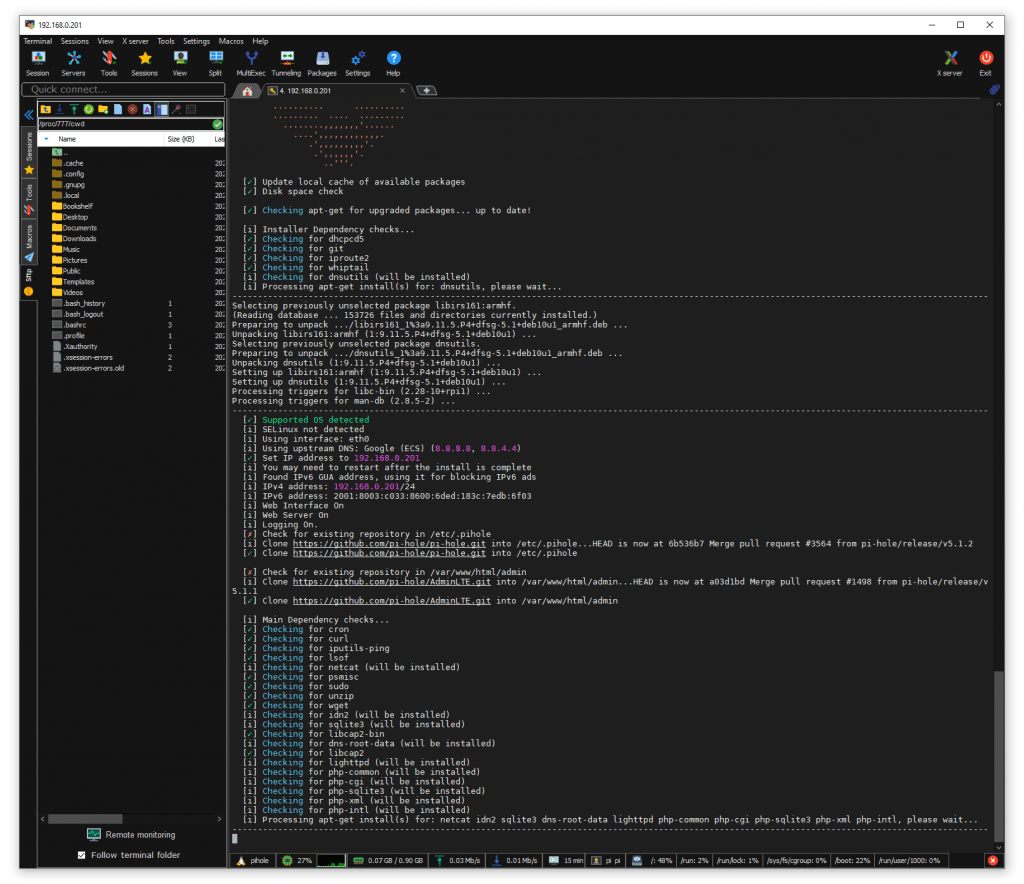
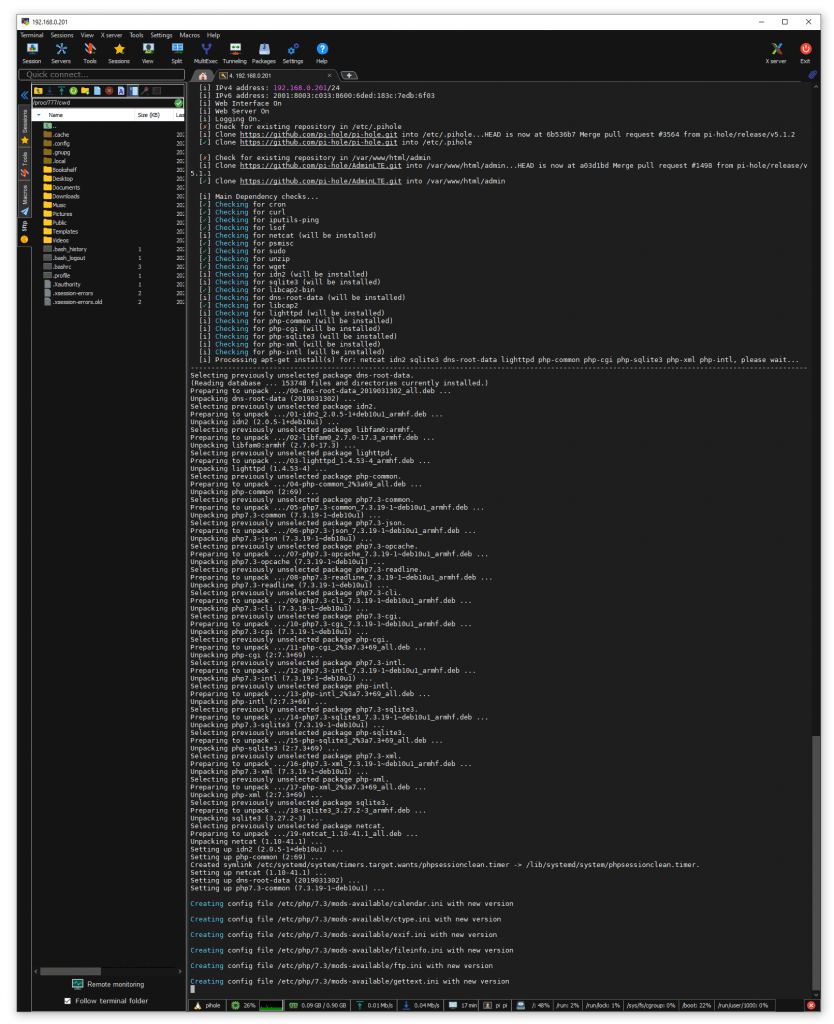
Installation took about 10 minutes
A PiHole admin URL and Password was displayed (write this down)
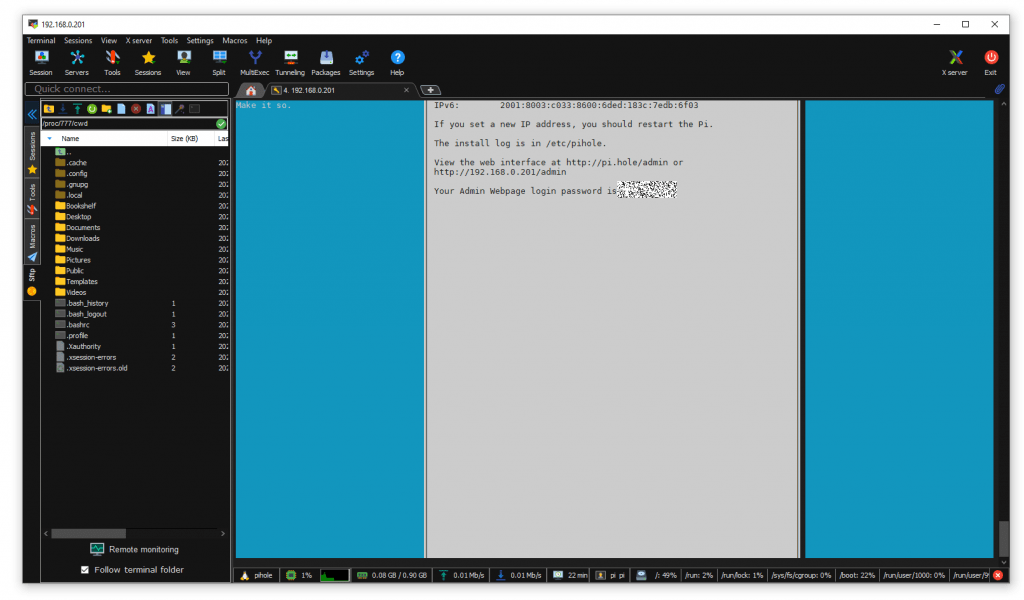
I loaded the PiHole initial admin screen (http://192.168.0.201/admin/) and it was a bit empty.
PiHole Interface
I logged into my PiHole (at http://192.1768.0.201/admin/) with the password provided during setup.
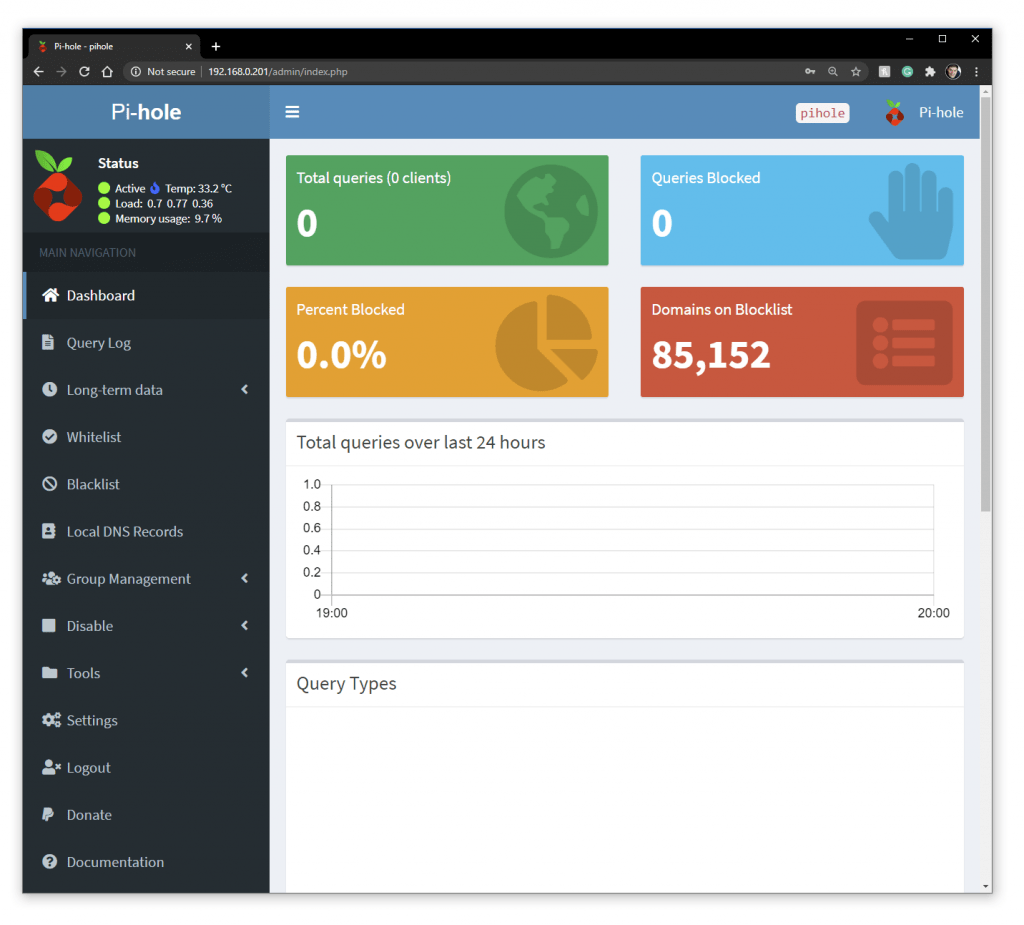
The Raspberry Pi Pi Hole service was up and waiting for connections
I have Zero traffic going through the PiHole.
Before I add computers on my network to the PiHole I had better uninstall the nextdns.io (my blog post about NextDNS.io here) as the Pi will now be the main DNS blocking Sinkhole in our house.
On my Windows 10 PC I added the DNS server for the PiHole in IPV4 and IPV6.
I obtained the PiHole IPV4 and IPV6 addresses (1) PiHole Admin, 2) Pi Hole Settings Page, 3) IP Address)
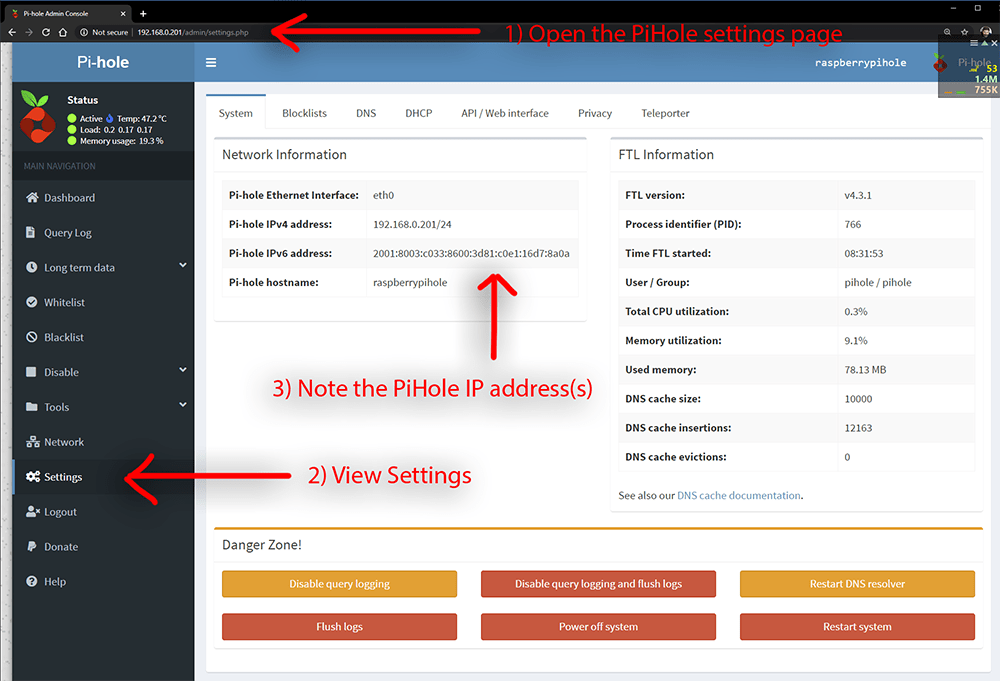
PiHole IPV4 and IPV6 addresses.
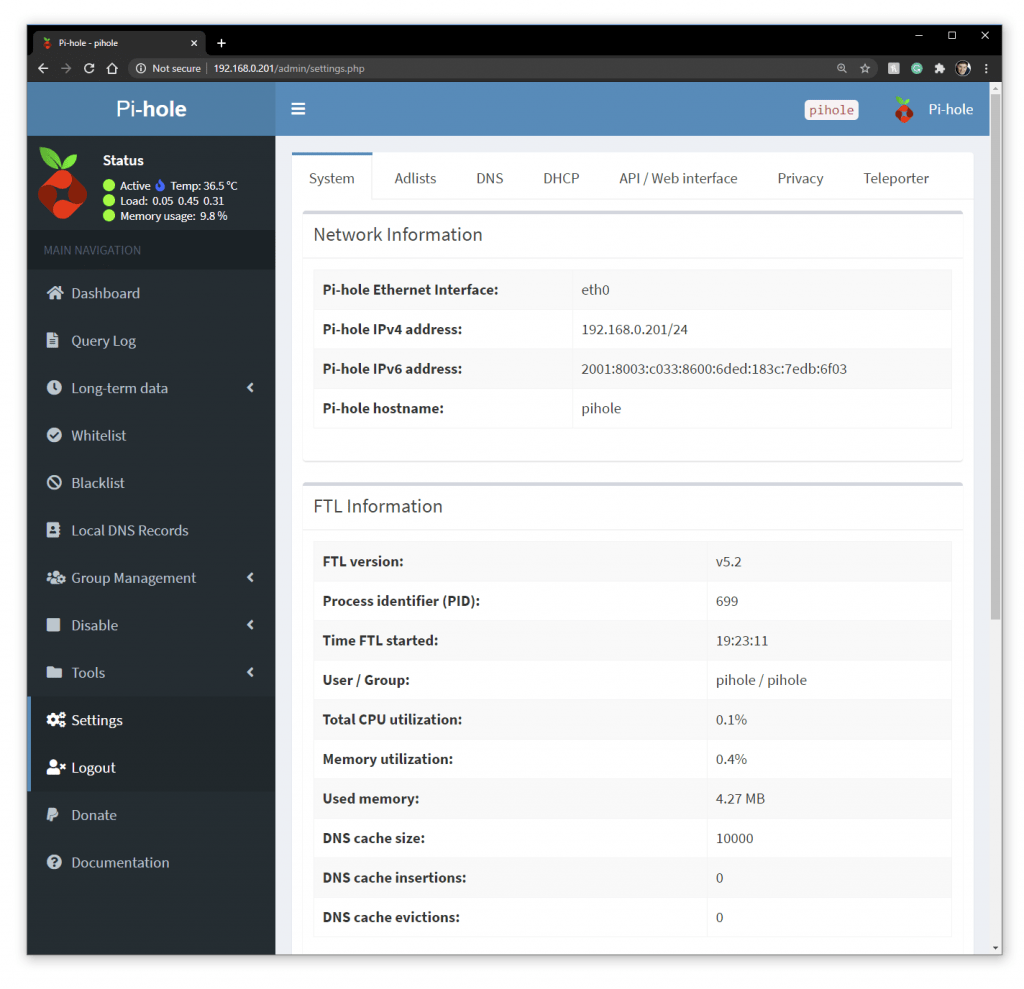
I added the Pi Holes IPV4 IP address to my Windows 10 IP Settings.
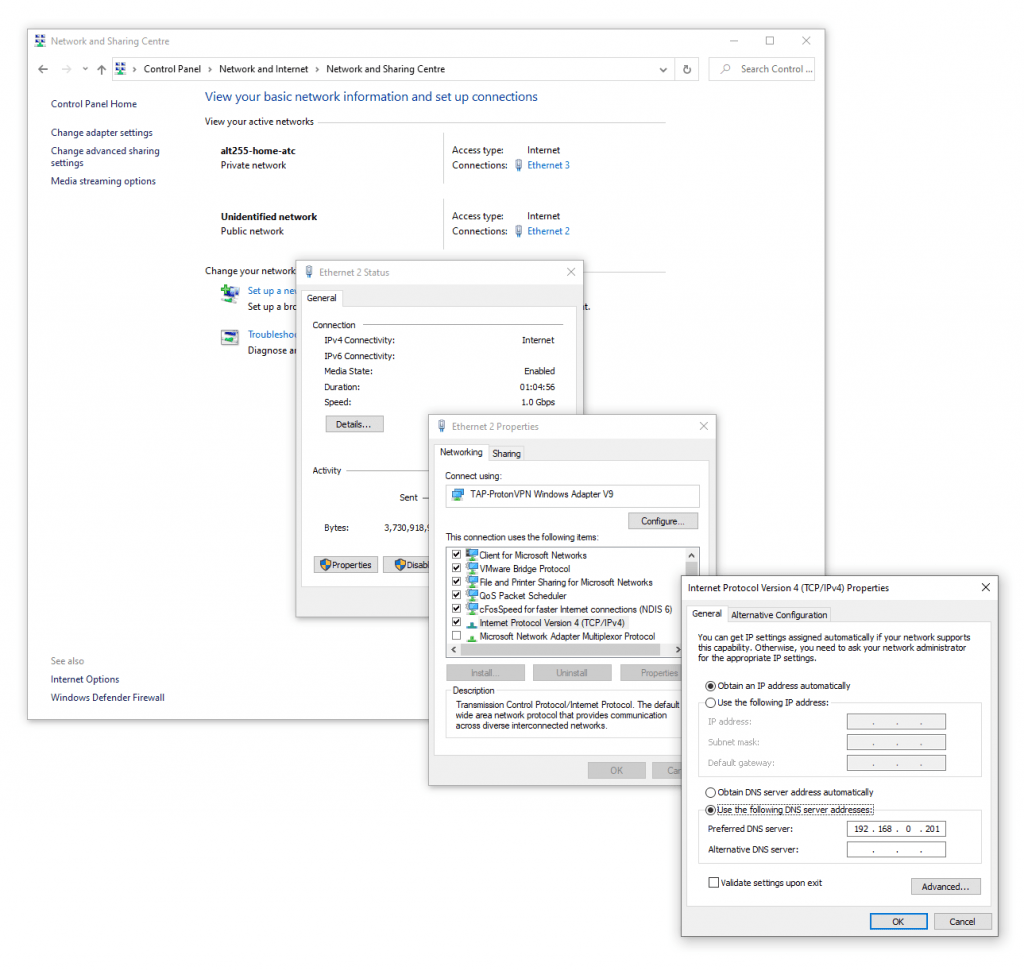
I added the Pi Holes IPV6 IP address to my Windows 10 IP Settings.
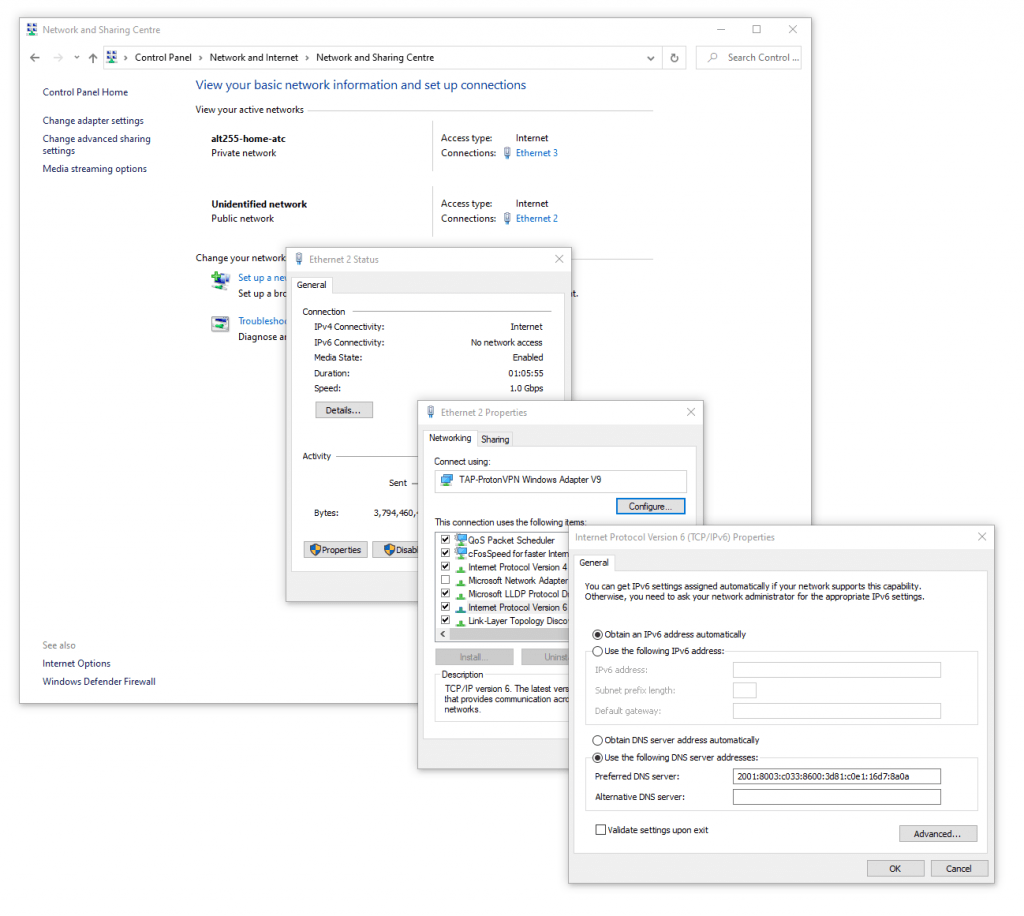
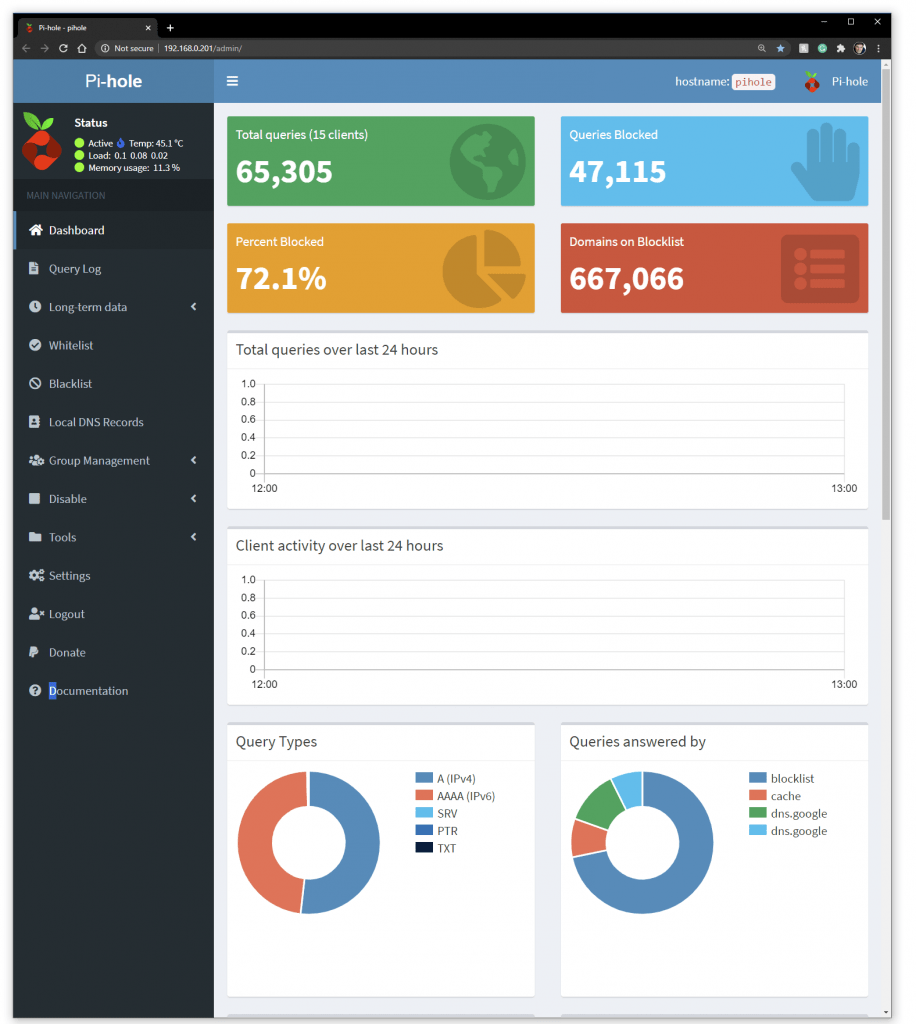
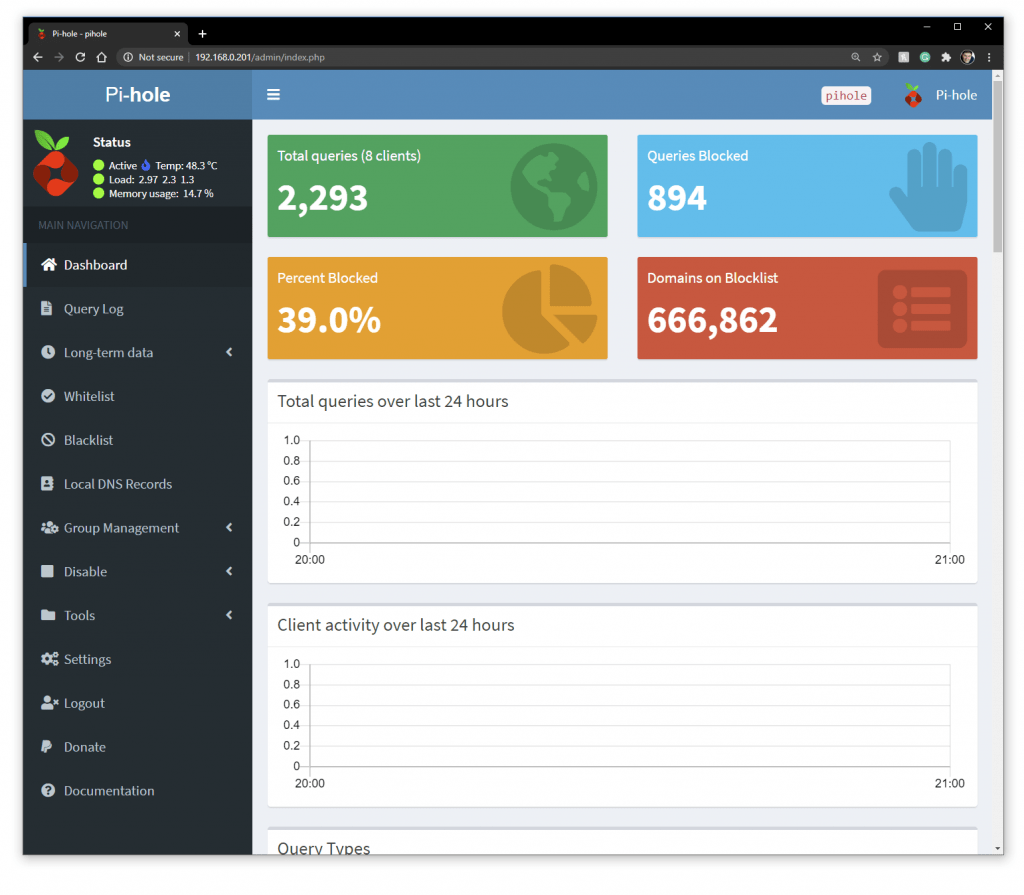
After 20 hours or rining computers through the Pi-Hole Admin interface I loaded the PiHole Admin Interface (at http://192.168.0.201/admin/index.php) was reporting stats.
I can view stats for Protocol and answered queries
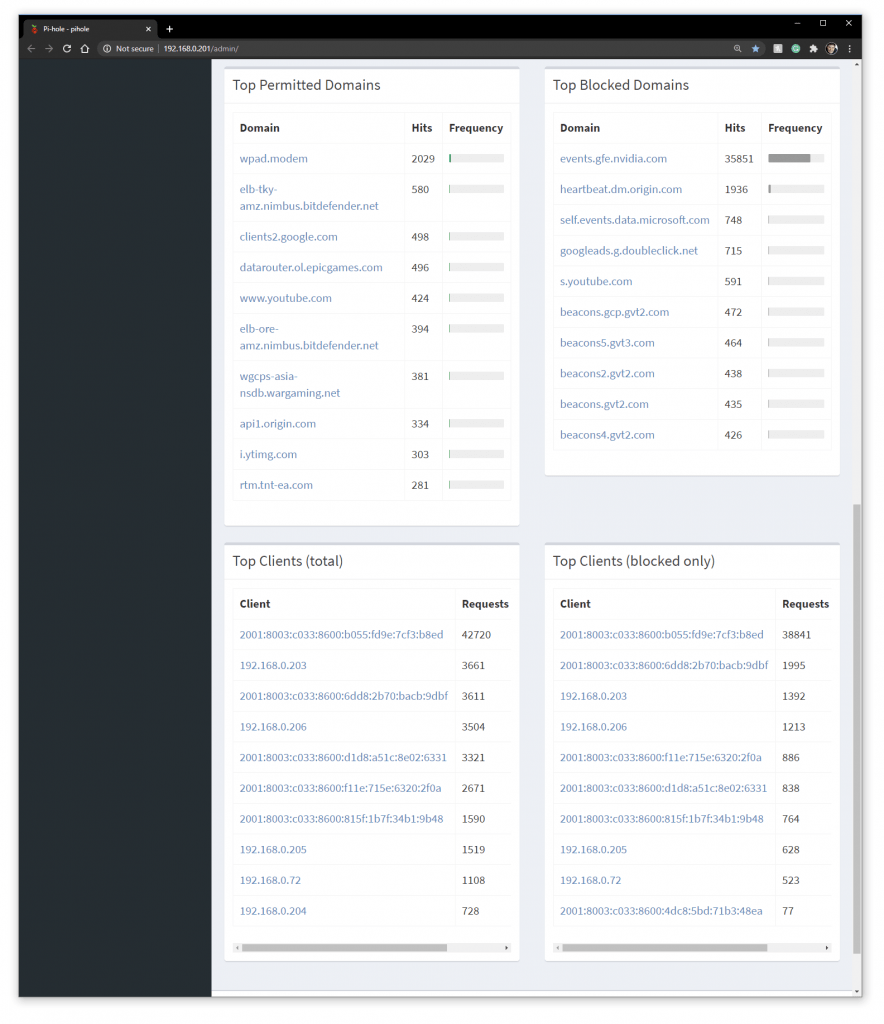
I can also see stats for permitted and blocked domains
Default Block Lists
I can also see the source blocked domains
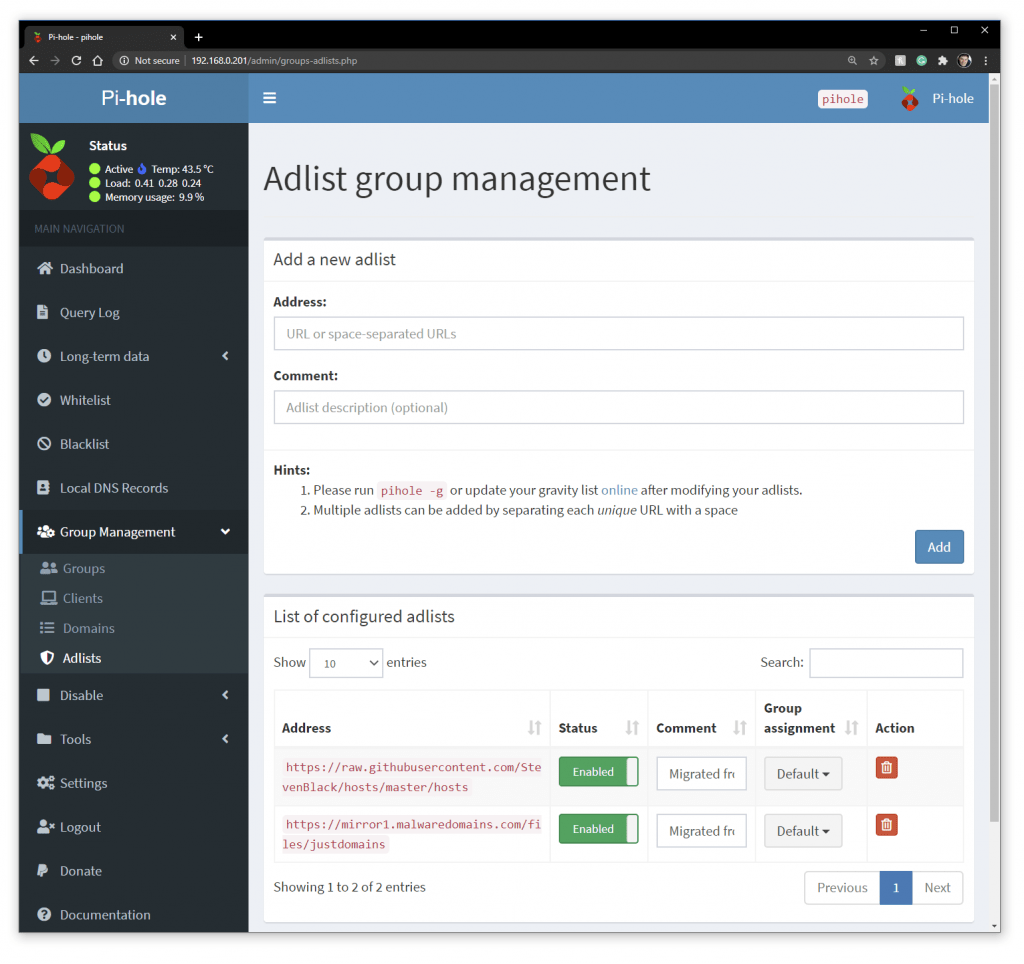
Add 3rd party block lists
I added these block lists to my PiHole list of sites to block (Thanks Jol)
https://v.firebog.net/hosts/Easyprivacy.txt
https://v.firebog.net/hosts/Prigent-Ads.txt
https://gitlab.com/quidsup/notrack-blocklists/raw/master/notrack-blocklist.txt
https://raw.githubusercontent.com/FadeMind/hosts.extras/master/add.2o7Net/hosts
https://raw.githubusercontent.com/crazy-max/WindowsSpyBlocker/master/data/hosts/spy.txt
https://www.github.developerdan.com/hosts/lists/ads-and-tracking-extended.txt
https://hostfiles.frogeye.fr/firstparty-trackers-hosts.txt
https://hostfiles.frogeye.fr/multiparty-trackers-hosts.txt
https://raw.githubusercontent.com/Perflyst/PiHoleBlocklist/master/android-tracking.txt
https://raw.githubusercontent.com/Perflyst/PiHoleBlocklist/master/SmartTV.txt
https://raw.githubusercontent.com/Perflyst/PiHoleBlocklist/master/AmazonFireTV.txt
https://v.firebog.net/hosts/Airelle-trc.txt
https://bitbucket.org/ethanr/dns-blacklists/raw/8575c9f96e5b4a1308f2f12394abd86d0927a4a0/bad_lists/Mandiant_APT1_Report_Appendix_D.txt
https://gist.githubusercontent.com/anudeepND/adac7982307fec6ee23605e281a57f1a/raw/5b8582b906a9497624c3f3187a49ebc23a9cf2fb/Test.txt
https://gitlab.com/quidsup/notrack-blocklists/raw/master/notrack-blocklist.txt
https://gitlab.com/quidsup/notrack-blocklists/raw/master/notrack-malware.txt
https://hosts-file.net/ad_servers.txt
https://hosts-file.net/emd.txt
https://hosts-file.net/exp.txt
https://hosts-file.net/grm.txt
https://hosts-file.net/psh.txt
https://isc.sans.edu/feeds/suspiciousdomains_Medium.txt
https://mirror1.malwaredomains.com/files/justdomains
https://mirror.cedia.org.ec/malwaredomains/immortal_domains.txt
http://someonewhocares.org/hosts/hosts
https://phishing.army/download/phishing_army_blocklist_extended.txt
https://ransomwaretracker.abuse.ch/downloads/CW_C2_DOMBL.txt
https://ransomwaretracker.abuse.ch/downloads/LY_C2_DOMBL.txt
https://ransomwaretracker.abuse.ch/downloads/RW_DOMBL.txt
https://ransomwaretracker.abuse.ch/downloads/TC_C2_DOMBL.txt
https://ransomwaretracker.abuse.ch/downloads/TL_C2_DOMBL.txt
https://raw.githubusercontent.com/crazy-max/WindowsSpyBlocker/master/data/hosts/spy.txt
https://raw.githubusercontent.com/crazy-max/WindowsSpyBlocker/master/data/hosts/win10/spy.txt
https://raw.githubusercontent.com/StevenBlack/hosts/master/data/add.2o7Net/hosts
https://raw.githubusercontent.com/StevenBlack/hosts/master/data/add.Risk/hosts
https://raw.githubusercontent.com/StevenBlack/hosts/master/data/add.Spam/hosts
https://raw.githubusercontent.com/StevenBlack/hosts/master/data/KADhosts/hosts
https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts
https://raw.githubusercontent.com/ZeroDot1/CoinBlockerLists/master/hosts
https://reddestdream.github.io/Projects/MinimalHosts/etc/MinimalHostsBlocker/minimalhosts
https://s3.amazonaws.com/lists.disconnect.me/simple_ad.txt
https://s3.amazonaws.com/lists.disconnect.me/simple_malvertising.txt
https://s3.amazonaws.com/lists.disconnect.me/simple_tracking.txt
https://v.firebog.net/hosts/AdguardDNS.txt
https://v.firebog.net/hosts/Airelle-hrsk.txt
https://v.firebog.net/hosts/Easylist.txt
https://v.firebog.net/hosts/Easyprivacy.txt
https://v.firebog.net/hosts/Prigent-Ads.txt
https://v.firebog.net/hosts/Prigent-Malware.txt
https://v.firebog.net/hosts/Prigent-Phishing.txt
https://v.firebog.net/hosts/Shalla-mal.txt
https://v.firebog.net/hosts/static/SamsungSmart.txt
https://v.firebog.net/hosts/static/w3kbl.txt
https://www.malwaredomainlist.com/hostslist/hosts.txt
https://www.squidblacklist.org/downloads/dg-malicious.acl
http://sysctl.org/cameleon/hosts
https://zerodot1.gitlab.io/CoinBlockerLists/hosts
https://zeustracker.abuse.ch/blocklist.php?download=domainblocklist
http://www.joewein.net/dl/bl/dom-bl.txt
http://www.networksec.org/grabbho/block.txt
I updated all block lists at http://192.168.0.201/admin/gravity.php
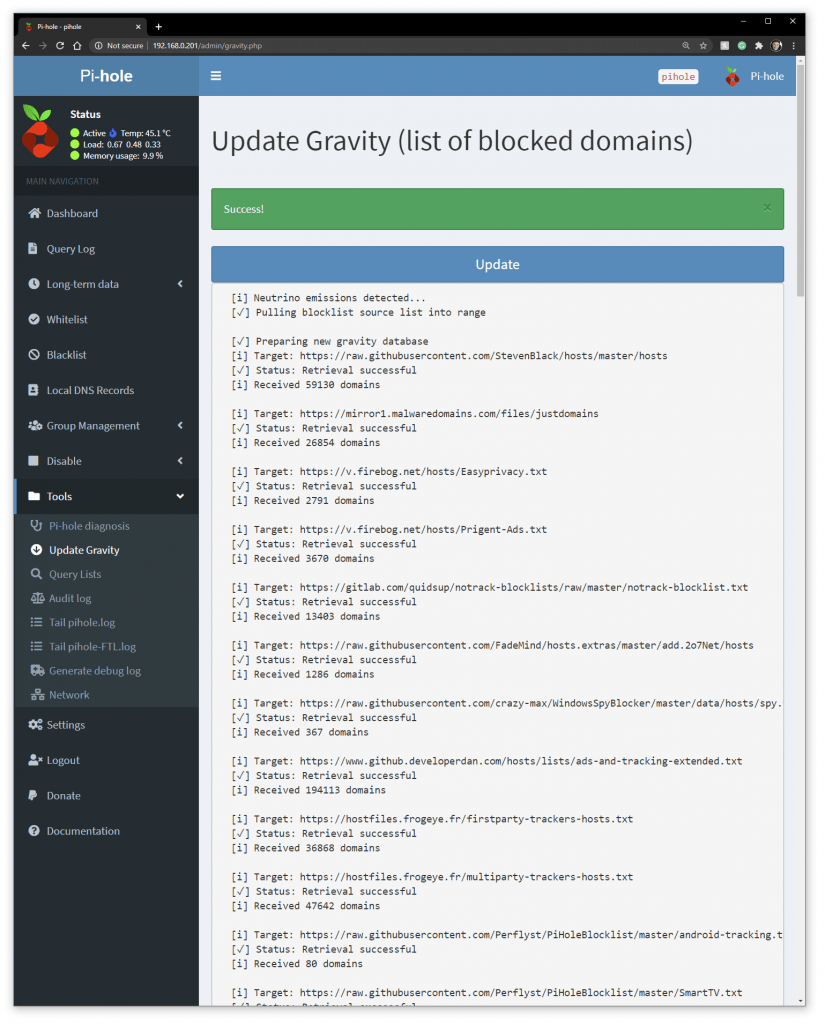
666,862 domains on my block list 🙂
I now have the Pi Hole blocking 666,862 domains, this number will increase as sites are added to the remote lists, nice.
LCD Screen Setup
I followed thin guide to setup the screen.
I can this code from the pi (logged in as root)
cd ~
wget https://raw.githubusercontent.com/adafruit/Raspberry-Pi-Installer-Scripts/master/adafruit-pitft.sh
chmod +x adafruit-pitft.sh
sudo ./adafruit-pitft.shI was prompted to choose a screen
Select configuration:
1. PiTFT 2.4", 2.8" or 3.2" resistive (240x320)
2. PiTFT 2.2" no touch (240x320)
3. PiTFT 2.8" capacitive touch (240x320)
4. PiTFT 3.5" resistive touch (320x480)
5. PiTFT Mini 1.3" or 1.54" display (240x240)
6. MiniPiTFT 1.14" display (240x135) - WARNING! CUTTING EDGE! WILL UPGRADE YOUR KERNEL TO LATEST
7. Quit without installing
SELECT 1-7:I entered “3” for PiTFT 2.8″ capacitive touch (240×320)
I then was prompted to set the rotation of the screen
Select rotation:
1. 90 degrees (landscape)
2. 180 degrees (portait)
3. 270 degrees (landscape)
4. 0 degrees (portait)
SELECT 1-4: I entered “3” for 270 degrees (landscape).
I was prompted to allow the console to appear on the screen
Would you like the console to appear on the PiTFT display? [y/n]
yInstall Summary
I rebooted
Reboot [y/n]
yI edited /boot/config.txt and changed these values
framebuffer_width=320
framebuffer_height=240Installing PADD to display PiHole stats on the LCD
I followed this guide to install PADD (the software that displays the PiHole stats on the LCD screen)
cd ~
wget -N https://github.com/jpmck/PADD/files/4320681/padd.txt
mv padd.txt paddsimon.sh
chmod +x paddsimon.shMaking PADD starts at boot
Edit this file
sudo nano ~/.bashrcand add the following to the end of the file
# Run PADD
# If we're on the PiTFT screen (ssh is xterm)
if [ "$TERM" == "linux" ] ; then
while :
do
/root/paddsimon.sh
sleep 0.2
done
fi
I rebooted the PI.
sudo showdown -r nowHow to Update the PiHole from the CLI
I ran the following command to update the PiHole block lists
pihole -gOutput…
[i] Pi-hole blocking is enabled
[i] Neutrino emissions detected...
[✓] Pulling blocklist source list into range
[i] Target: raw.githubusercontent.com (hosts)
[✓] Status: Retrieval successful
[i] Target: mirror1.malwaredomains.com (justdomains)
[✓] Status: No changes detected
[i] Target: sysctl.org (hosts)
[✓] Status: No changes detected
[i] Target: s3.amazonaws.com (simple_tracking.txt)
[✓] Status: No changes detected
[i] Target: s3.amazonaws.com (simple_ad.txt)
[✓] Status: No changes detected
[i] Target: hosts-file.net (ad_servers.txt)
[✓] Status: No changes detected
[i] Target: raw.githubusercontent.com (ytadblock.txt)
[✓] Status: Retrieval successful
[i] Target: v.firebog.net (Easyprivacy.txt)
[✓] Status: No changes detected
[i] Target: v.firebog.net (Prigent-Ads.txt)
[✓] Status: No changes detected
[i] Target: gitlab.com (notrack-blocklist.txt)
[✓] Status: Retrieval successful
[i] Target: raw.githubusercontent.com (hosts)
[✓] Status: Retrieval successful
[i] Target: raw.githubusercontent.com (spy.txt)
[✓] Status: Retrieval successful
[i] Target: www.github.developerdan.com (ads-and-tracking-extended.txt)
[✓] Status: Retrieval successful
[i] Target: hostfiles.frogeye.fr (firstparty-trackers-hosts.txt)
[✓] Status: Retrieval successful
[i] Target: hostfiles.frogeye.fr (multiparty-trackers-hosts.txt)
[✓] Status: Retrieval successful
[i] Target: raw.githubusercontent.com (android-tracking.txt)
[✓] Status: Retrieval successful
[i] Target: raw.githubusercontent.com (SmartTV.txt)
[✓] Status: Retrieval successful
[i] Target: raw.githubusercontent.com (AmazonFireTV.txt)
[✓] Status: Retrieval successful
[i] Target: v.firebog.net (Airelle-trc.txt)
[✓] Status: No changes detected
[i] Target: bitbucket.org (Mandiant_APT1_Report_Appendix_D.txt)
[✓] Status: No changes detected
[i] Target: gist.githubusercontent.com (Test.txt)
[✓] Status: Retrieval successful
[i] Target: gitlab.com (notrack-malware.txt)
[✓] Status: Retrieval successful
[i] Target: hosts-file.net (emd.txt)
[✓] Status: No changes detected
[i] Target: hosts-file.net (exp.txt)
[✓] Status: No changes detected
[i] Target: hosts-file.net (grm.txt)
[✓] Status: No changes detected
[i] Target: hosts-file.net (psh.txt)
[✓] Status: No changes detected
[i] Target: isc.sans.edu (suspiciousdomains_Medium.txt)
[✓] Status: Retrieval successful
[i] Target: mirror.cedia.org.ec (immortal_domains.txt)
[✓] Status: No changes detected
[i] Target: someonewhocares.org (hosts)
[✓] Status: No changes detected
[i] Target: phishing.army (phishing_army_blocklist_extended.txt)
[✓] Status: Retrieval successful
[i] Target: ransomwaretracker.abuse.ch (CW_C2_DOMBL.txt)
[✓] Status: Retrieval successful
[i] Target: ransomwaretracker.abuse.ch (LY_C2_DOMBL.txt)
[✓] Status: Retrieval successful
[i] Target: ransomwaretracker.abuse.ch (RW_DOMBL.txt)
[✓] Status: Retrieval successful
[i] Target: ransomwaretracker.abuse.ch (TC_C2_DOMBL.txt)
[✓] Status: Retrieval successful
[i] Target: ransomwaretracker.abuse.ch (TL_C2_DOMBL.txt)
[✓] Status: Retrieval successful
[i] Target: raw.githubusercontent.com (spy.txt)
[✗] Status: Not found
[✗] List download failed: no cached list available
[i] Target: raw.githubusercontent.com (hosts)
[✓] Status: Retrieval successful
[i] Target: raw.githubusercontent.com (hosts)
[✓] Status: Retrieval successful
[i] Target: raw.githubusercontent.com (hosts)
[✓] Status: Retrieval successful
[i] Target: raw.githubusercontent.com (hosts)
[✓] Status: Retrieval successful
[i] Target: raw.githubusercontent.com (hosts)
[✗] Status: Not found
[✗] List download failed: no cached list available
[i] Target: reddestdream.github.io (minimalhosts)
[✓] Status: No changes detected
[i] Target: s3.amazonaws.com (simple_malvertising.txt)
[✓] Status: Retrieval successful
[i] Target: v.firebog.net (AdguardDNS.txt)
[✓] Status: No changes detected
[i] Target: v.firebog.net (Airelle-hrsk.txt)
[✓] Status: No changes detected
[i] Target: v.firebog.net (Easylist.txt)
[✓] Status: No changes detected
[i] Target: v.firebog.net (Prigent-Malware.txt)
[✓] Status: No changes detected
[i] Target: v.firebog.net (Prigent-Phishing.txt)
[✓] Status: No changes detected
[i] Target: v.firebog.net (Shalla-mal.txt)
[✓] Status: No changes detected
[i] Target: v.firebog.net (SamsungSmart.txt)
[✓] Status: No changes detected
[i] Target: v.firebog.net (w3kbl.txt)
[✓] Status: No changes detected
[i] Target: www.malwaredomainlist.com (hosts.txt)
[✓] Status: No changes detected
[i] Target: www.squidblacklist.org (dg-malicious.acl)
[✗] Status: Connection Timed Out (Cloudflare)
[✗] List download failed: no cached list available
[i] Target: zerodot1.gitlab.io (hosts)
[✓] Status: No changes detected
[i] Target: zeustracker.abuse.ch (blocklist.php?download=domainblocklist)
[✓] Status: Retrieval successful
[i] Target: www.joewein.net (dom-bl.txt)
[✓] Status: Retrieval successful
[i] Target: www.networksec.org (block.txt)
[✓] Status: Retrieval successful
[i] Received empty file: using previously cached list
[✓] Consolidating blocklists
[✓] Extracting domains from blocklists
[i] Number of domains being pulled in by gravity: 1178534
[✓] Removing duplicate domains
[i] Number of unique domains trapped in the Event Horizon: 954486
[i] Number of whitelisted domains: 2
[i] Number of blacklisted domains: 0
[i] Number of regex filters: 0
[✓] Parsing domains into hosts format
[✓] Cleaning up stray matter
[✓] Force-reloading DNS service
[✓] DNS service is running
[✓] Pi-hole blocking is Enabled
I can view all possible command line options by running
pihole /?Output..
Usage: pihole [options]
Example: 'pihole -w -h'
Add '-h' after specific commands for more information on usage
Whitelist/Blacklist Options:
-w, whitelist Whitelist domain(s)
-b, blacklist Blacklist domain(s)
--wild, wildcard Wildcard blacklist domain(s)
--regex, regex Regex blacklist domains(s)
Add '-h' for more info on whitelist/blacklist usage
Debugging Options:
-d, debug Start a debugging session
Add '-a' to enable automated debugging
-f, flush Flush the Pi-hole log
-r, reconfigure Reconfigure or Repair Pi-hole subsystems
-t, tail View the live output of the Pi-hole log
Options:
-a, admin Web interface options
Add '-h' for more info on Web Interface usage
-c, chronometer Calculates stats and displays to an LCD
Add '-h' for more info on chronometer usage
-g, updateGravity Update the list of ad-serving domains
-h, --help, help Show this help dialog
-l, logging Specify whether the Pi-hole log should be used
Add '-h' for more info on logging usage
-q, query Query the adlists for a specified domain
Add '-h' for more info on query usage
-up, updatePihole Update Pi-hole subsystems
Add '--check-only' to exit script before update is perfo rmed.
-v, version Show installed versions of Pi-hole, Web Interface & FTL
Add '-h' for more info on version usage
uninstall Uninstall Pi-hole from your system
status Display the running status of Pi-hole subsystems
enable Enable Pi-hole subsystems
disable Disable Pi-hole subsystems
Add '-h' for more info on disable usage
restartdns Restart Pi-hole subsystems
checkout Switch Pi-hole subsystems to a different Github branch
Add '-h' for more info on checkout usage
After 1 Week
After 1 week stats were rolling into the PIHole.
40% of all traffic was being blocked.
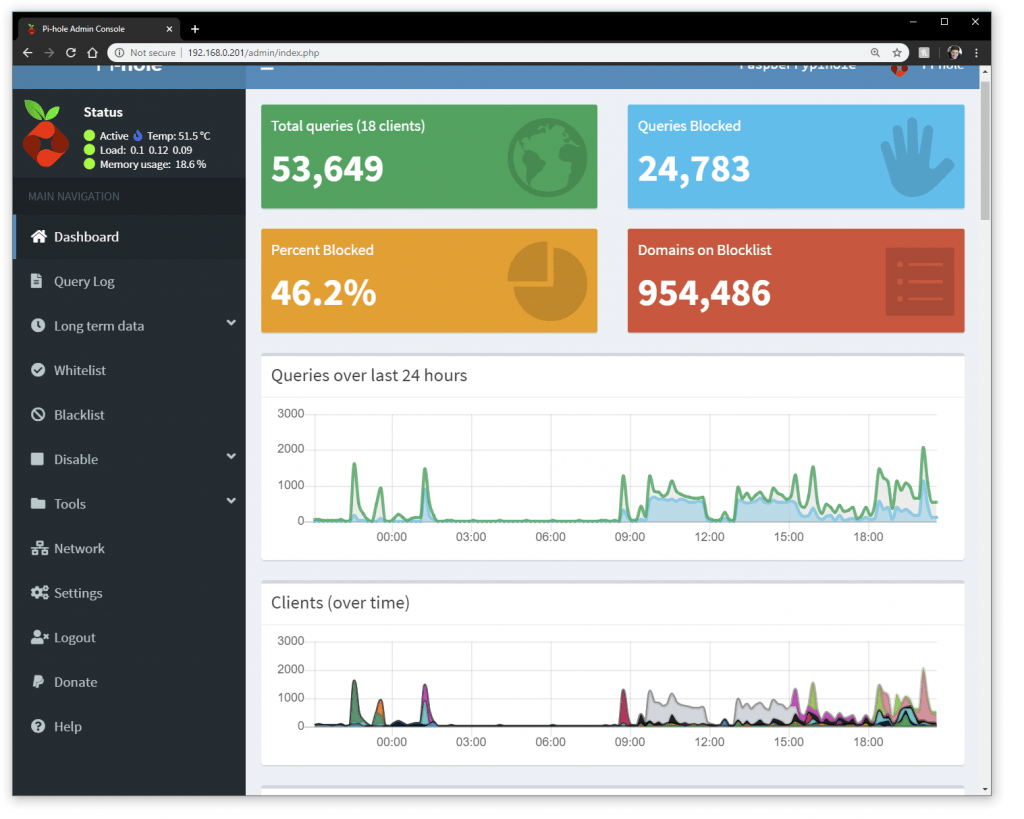
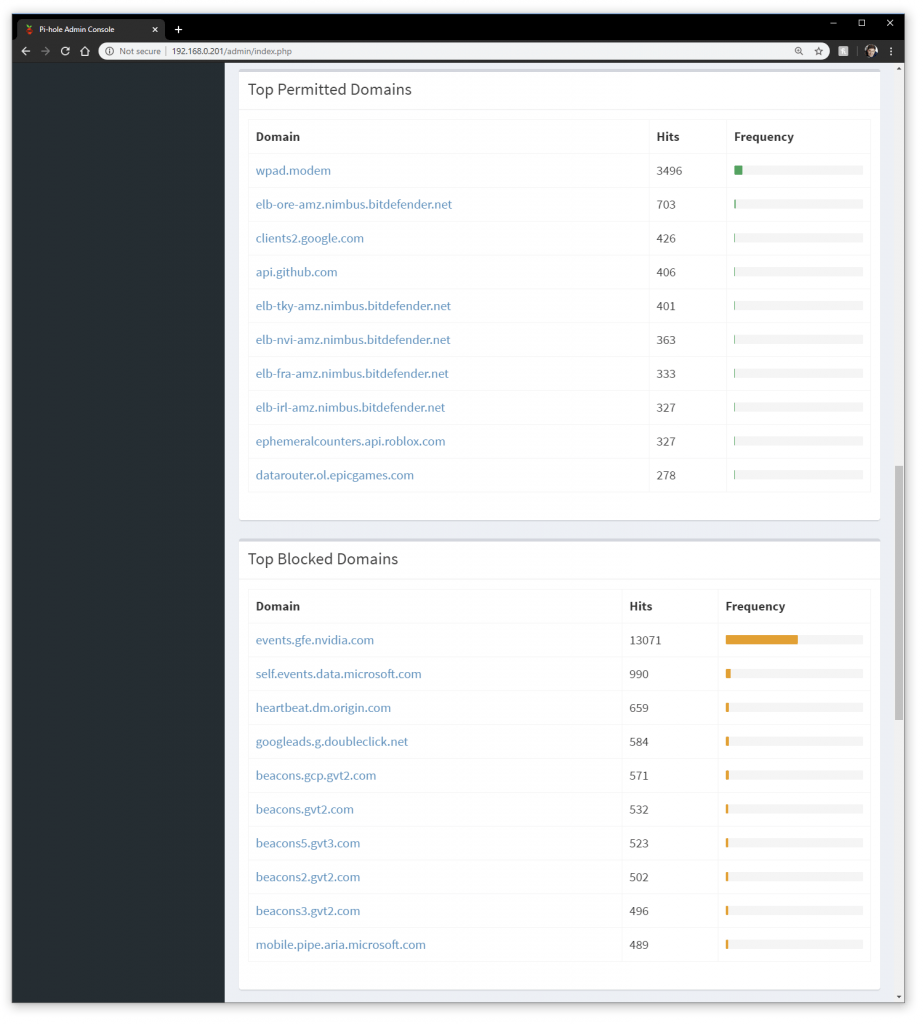
I could see blocked and allowed domain calls
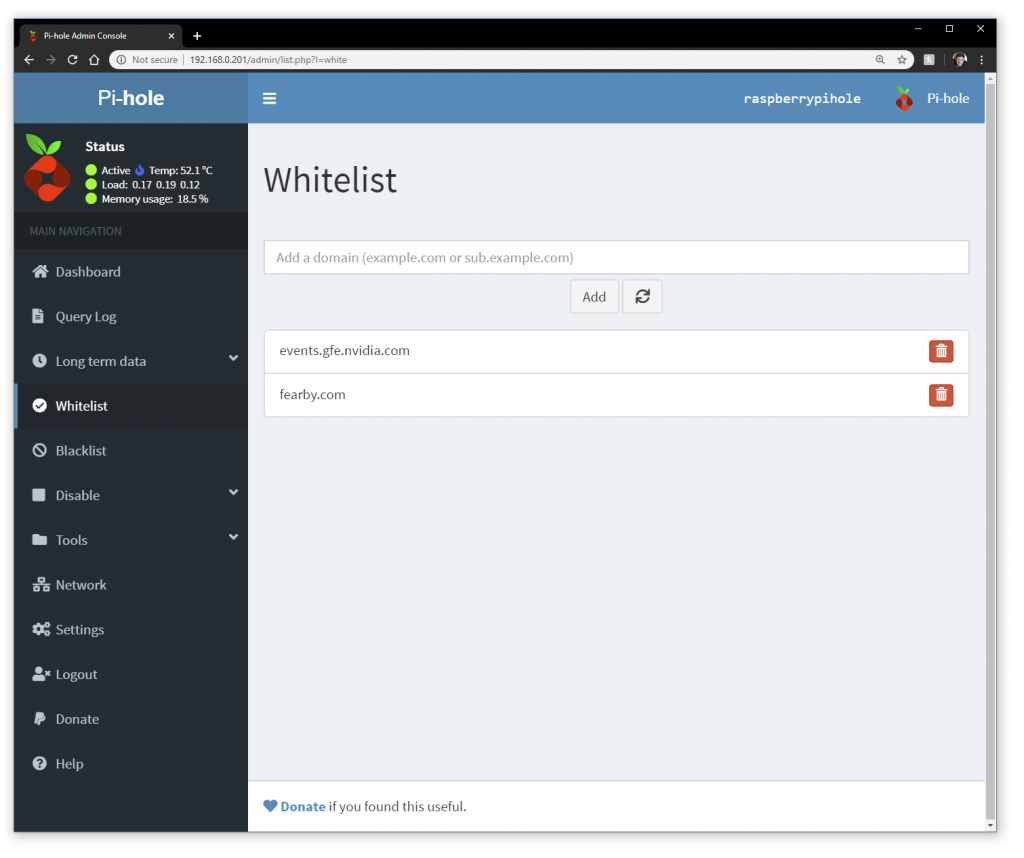
I can white list domains if they are blocked.
Done
This is what it looks like done
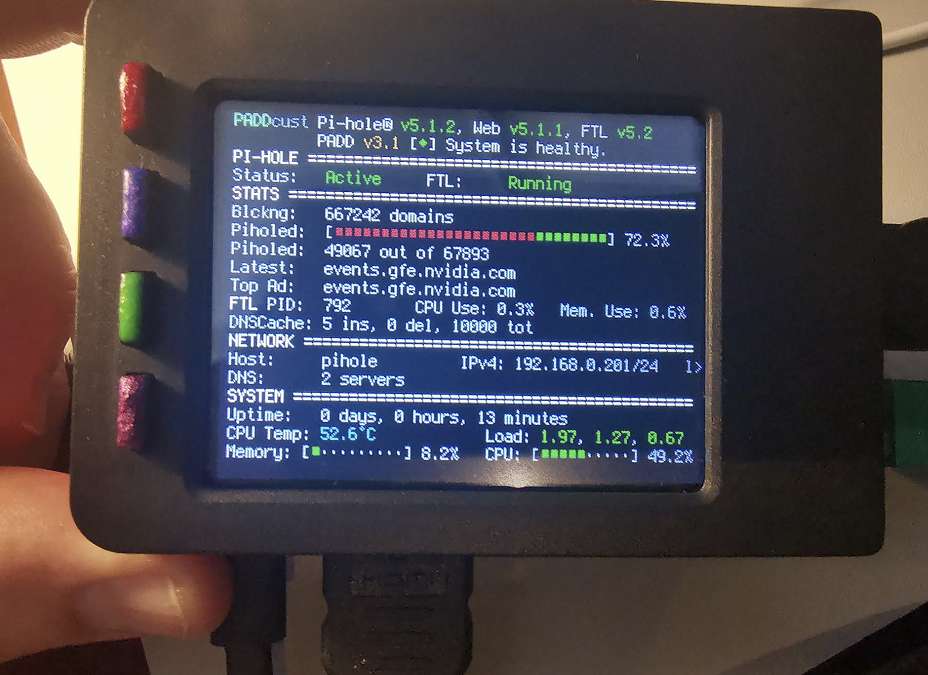
Nice
Did it block Ad’s
Mostly Yes. Not all advertisements are blocked but most are.
Some YouTube Advertisements seem to get through but I am seeing far less Advertisements in web pages
Using Python to use buttons on the PiTFT Plus 320×240 TFT Touchscreen with a PiHole
Read this guide to make the buttons word: Using Python to use buttons on the PiTFT Plus 320×240 TFT Touchscreen with a PiHole
Troubleshooting
If you receive an update about updating languages on your first boot while updating you can manually update all software by running this after you first reboot in a Terminal window.
sudo apt-get update && apt-get full-upgradeIf your Micro SD cad is filling up you can run to free some space
sudo apt cleanI needed to white list “events.gfe.nvidia.com” to allow my video card drivers to upodate.
Cooling
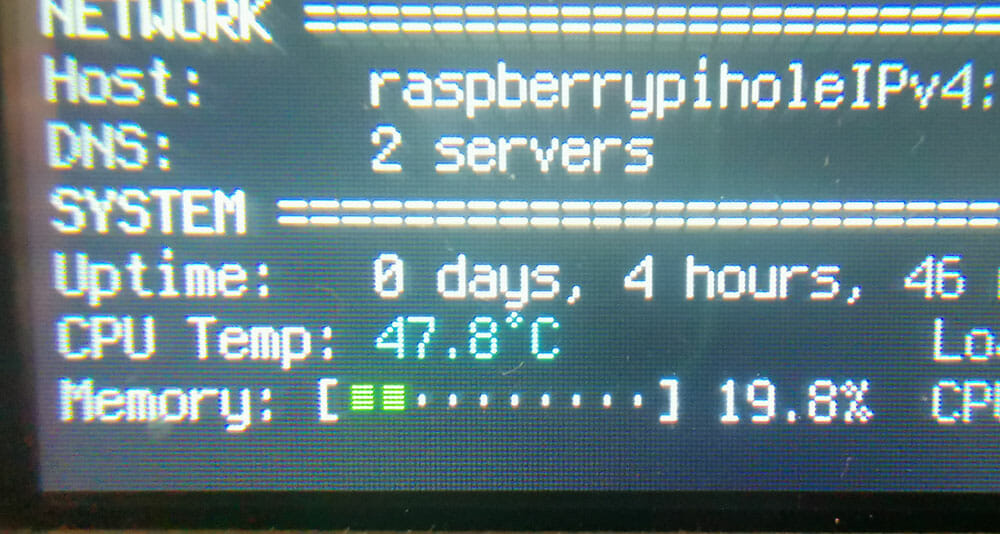
The Raspberry Pi is running cool at 47c (even though it is in a tight space).
I might add a heat pipe to it and have an external fan. I will thermal epoxy the hat pipe to the Pi CPU and run it outside to a external heat sink and fan.
I have many spare heat sinks laying around.

I will update when the part’s arrive.
Update: I did not end up adding extra cooling, there was no need in summer.
Rotating the screen
I did exit my /boot/config.txt to rotate my LCD Screen orientation
Buttons
Read this guide to see how I setup a Python script to make my buttons work.
Do edit your /boot.config.txt to configure your screen rotation (if need be) and to check if the LCD screen is setup (by Adafruit)
framebuffer_width=240
framebuffer_height=320Backup and Restore PiHole Settings
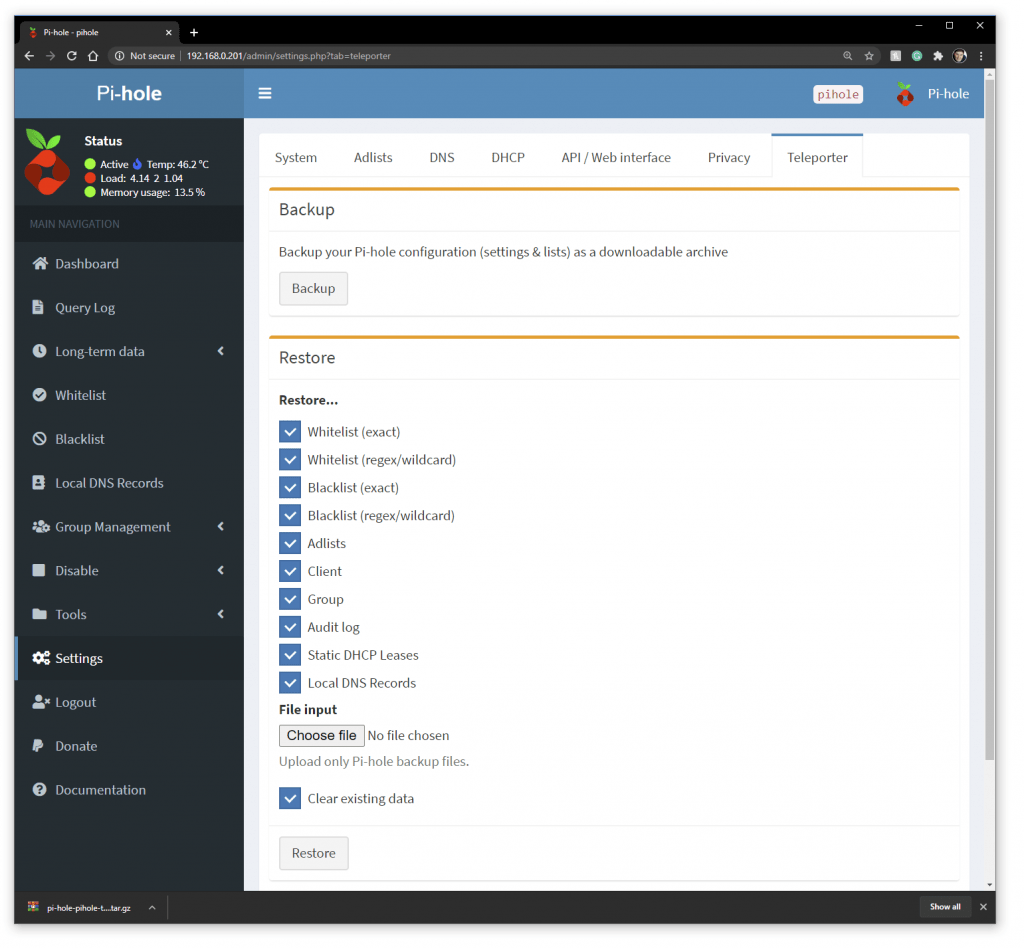
I used the PiHole Backup feature (at http://192.168.0.201/admin/settings.php?tab=teleporter) to backup all of my PiHole Settings to a zip file.
Handy Links
Handy Guide: https://learn.adafruit.com/pi-hole-ad-pitft-tft-detection-display/pitft-configuration to configure the LCD Screen
Schematics of the screen: https://learn.adafruit.com/assets/25555
Donate to PiHole: https://pi-hole.net/donate/
Raspberry Pi GPIO Pins: https://www.raspberrypi.org/documentation/usage/gpio/
v 2.3 Updating to PiHole 5.1.2